How to Prepare for a Career in Cyber Security
Skip to>>Our comprehensive list of cyber security scholarships
If you’re reading this page, then you probably already have a notion of how explosive the growth of opportunity within cyber security has been over the past few years. One of the fastest growing technology fields — which are some of the fastest growing job sets in the world — cyber security had over 1,000,000 job openings in America just last year. While you may have a notion that you would like to pursue a career in cyber security, there are still a few things you need to decide to clarify exactly what sort of position you would like to prepare for. Cyber security is a wide and varied set of jobs, everything from pure management to researching new threats, to responding to a massive attack in real time. Below you will see a variety of ways to sort cyber security positions, based on pay, experience level, job responsibilities, and education required. We hope that our outline below can help to point you in the most productive direction for achieving your goals. For some, that might be returning to school, while others might elect to work on projects on the site or spend a little longer gaining experience in their current position. Check out our guide on how to prepare for a career in cyber security below.
There is an expected shortfall of 1.5 million skilled security professionals by 2020. — Booz Allen Hamilton Study
Discerning Which Cyber Security Job is a Good Fit Based on Educational Requirements
While many cyber security careers require on-the-job training, there are a number of cyber security degree options available at each level. By discerning what degree level you might be interested in, you’ve already narrowed down the number of cyber security careers that you may automatically quality for.
Associates Degrees
Associate degrees in cyber security examine computer information technology, Cisco networking, network security and more. Associate degrees prepare individuals for entry level positions related to computer support, programming, help desk, IT, and network administration. For further information on where your associate degree can take you check out our resource on the types of associates degrees you can obtain related to cyber security here .
Bachelor’s Degrees
Bachelor’s degrees in cyber security offer an even wider range of classes and open many more doors towards employment. Topics covered in a cyber security bachelor’s degree may include information assurance management (IAM), technology, IT, network infrastructure, software development, network security, forensic, and tactics to defeat cyber crime. Bachelor’s degrees prepare individuals for mid to upper level positions like an information security analyst, computer support specialist, cryptographer, forensic expert, and much more. For more information on what you can do with your bachelor’s in cyber security we recommend you check here .
Master’s Degrees
While years of experience, particularly in cyber security due to the versatility of skills required, are essential for landing an upper level position in cyber security, a master’s degree in cyber and information security is also a core component. These master’s degrees in cyber security are a fantastic way to stand out and secure advancement in your career. Topics covered in a cyber security master’s degree may include information assurance, information assurance for mobile devices, internal protection, vulnerability mitigation, assured software analytics, cryptography and more. Master’s in Cyber Security related fields can help to prepare you for senior level roles, or enable you to step into mid level roles with less experience. For more information on what to do with your master’s in cyber security check here
Doctoral Degrees
If you decide to further your education with a doctoral degree in cyber security that means you are more-than-likely ready to continue your career through research projects or are seeking policy roles for the future. Doctoral programs like these prepare you for a leadership role in information assurance and cyber security. Some of these programs will continue to train in advanced technical skills and utilize your work/ life experiences. These doctoral programs work well for individuals who are ready to think outside of the cyber security box and who innovate solutions for information assurance.
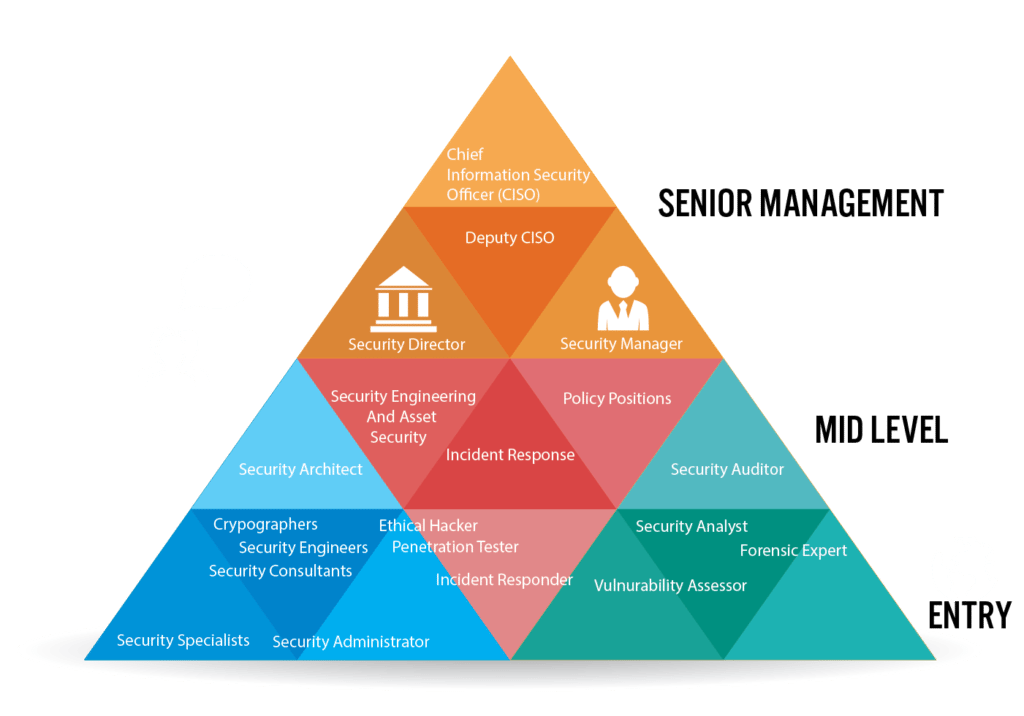
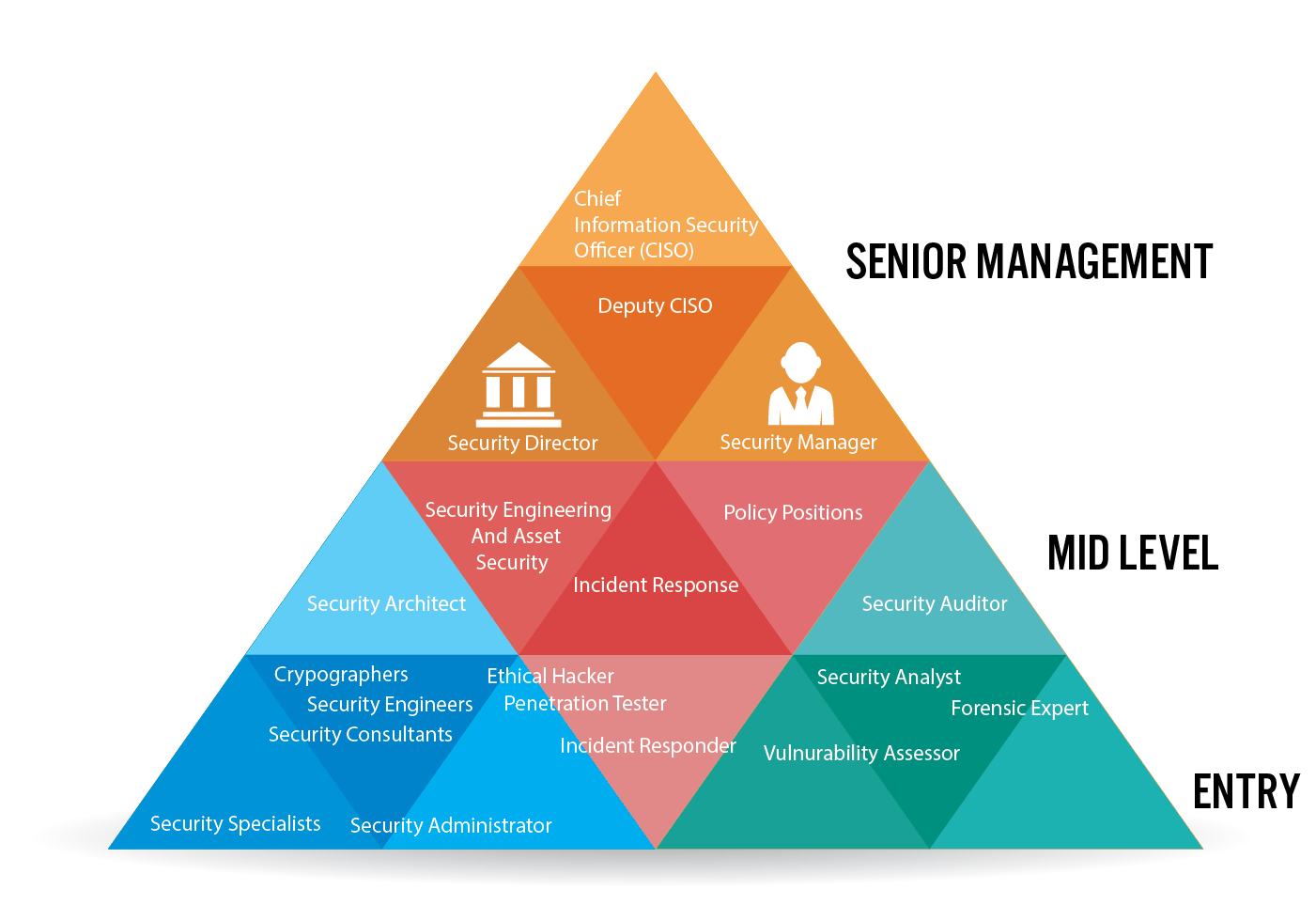
Determining Future Plans by Examining Cyber Security Career Progressions
Choosing a career in cyber security will often times directly correlate with the experience you have already. Whether you have experience managing individuals in IT firms, security guard experience, or linguistics, matching your skills to the right degree and the right position are essential. For many of the degrees below it is essential to arrive equipped with prerequisite skills though many of the skills are actually acquired on-the-job. Sound a little like a chicken and egg scenario? It’s not really. Like with many fields, working your way up into the desired role is how you gain that experience.
Common Paths
While some technology or management experience (even outside of cyber security) and an information assurance degree can help you segue directly into a mid or upper-level cyber security role, more commonly individuals work their way up though a few common paths.
- Entry level jobs requiring associates and bachelors can often position you to work up through the engineering ranks of a cyber organization. Check out careers such as network administrator, system administrator, junior security developer, or security administrator for good options for this path.
- For those who like to be at the center of all the action, the incident response vertical of cyber security organizations can often be entered with a bachelors degree in cyber security. Additional experience and certifications further pave the way for advancement in this vertical.
- For those seeking policy roles, security analyst careers can start with information assurance bachelors. Information assurance bachelors are often very similar to cyber security bachelors, but focus slightly more on policy aspects of cyber security. Alternatively, studying forensic computing can help you to land a job in a government agency or crime fighting unit, another way to enter into policy from the bottom.
- For those with management experience and a few years experience with cyber security, a masters degree or a few certifications can often land you a job as a security architect. Security architects are often the head technical leads over an organization’s cyber security products.
Deciding your path by salary
For many professionals, the intended path may have dollar signs attached. Knowing what you need to support yourself and your family is a huge motivator. Below we have organized common cyber security careers by salary.
A security architect is the individual responsible for maintaining the security of a company’s computer system. They must think like hackers to anticipate many of the tactics used to gain unauthorized access.
Information security analysts plan and implement security measures to protect an organization’s computer networks and systems. Their responsibilities continually expand along with the increase in cyber attacks.