Cyber Security professionals are one of the most in-demand worker types in information technology and systems professionals.
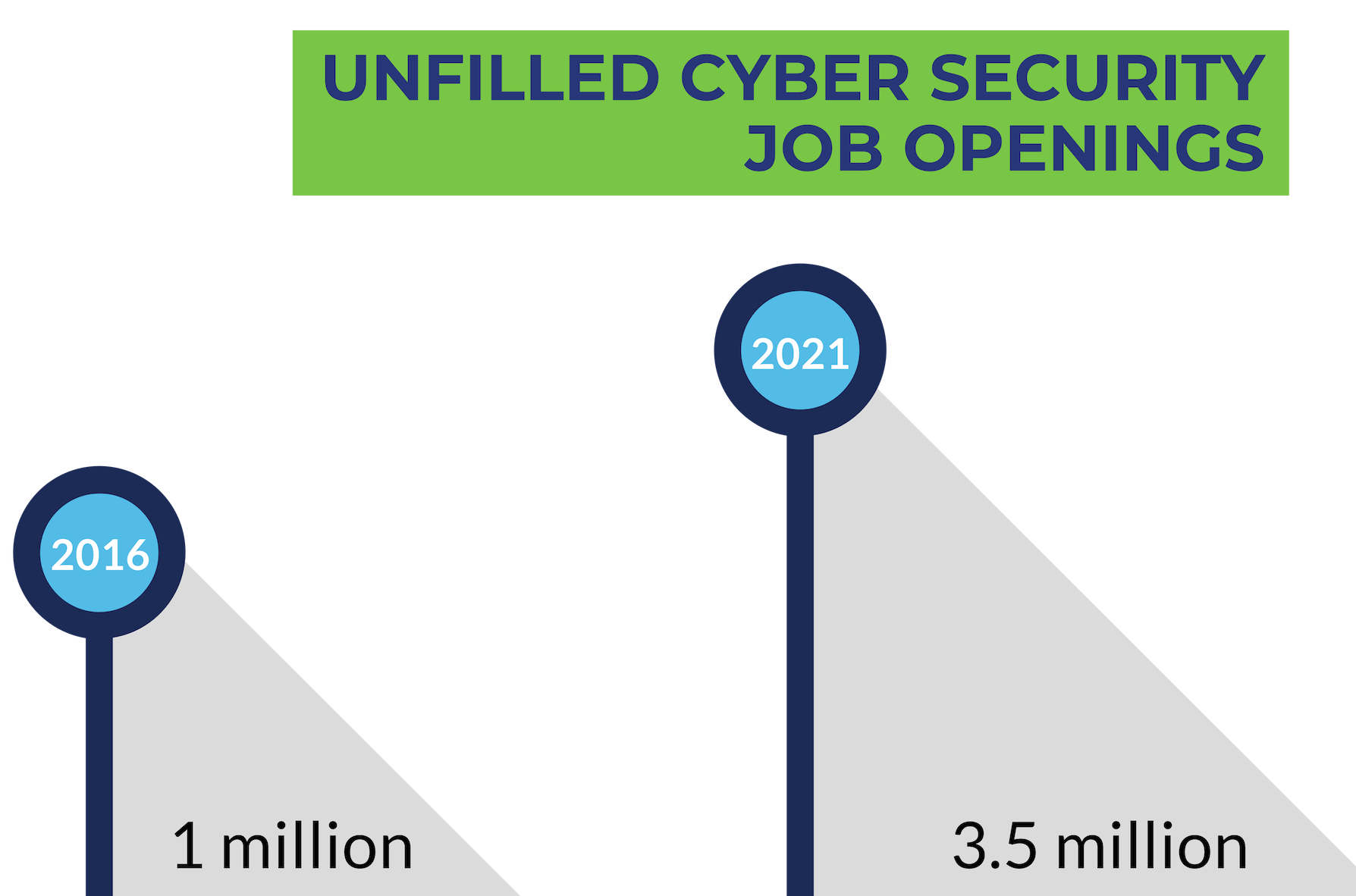
In 2016, a full million cyber security job openings were unfilled in America, and the ‘job gap’ is only expected to get bigger. By 2021, this gap is expected to grow to 3.1 million jobs.
And while cyber security can be quite a challenging (and rewarding) field, the barrier to entry is lower than many other fields. Lucrative careers can be born out of cyber security-related degrees at the associates through doctoral levels of study.
Additionally, cyber security jobs come in all types. There are roles in cyber security for professionals that are good at programming, reverse engineering, forensic analysis, management, general configuration of hardware, judgment on tight timelines, who are interested in privacy, or the creation of new products.
With the proper training and work ethic, many cyber security niches are accessible to many, many people.
We’ve covered a wide range of career-based topics on CyberSecurityDegrees.com, many of which are listed below. We recommend finding a section of jobs that particularly appeals to you below, reading through a few quick summaries of common job types, and then diving deeper through our in-depth career guides.
Find our guides to specific degrees below, or for more information on common career progressions and general preparatory materials, check out our guide to preparing for a career in cyber security.
Below we’ll guide you through the major categories of cyber security career including the following:
Entry-Level Careers
While many of the careers listed below can be entered early in your career in cyber security, for some getting into cyber security requires an intermediate step. Careers such as IT Help Desk, Network Administrator, Systems Administrator, or software engineer help many people segue into cyber security. Alternatively, those that are already working roles listed below may find opportunities to volunteer for or request more cyber security-related tasks. Over time, they may find themselves transitioning into a more cyber security-centered role.
IT help desk jobs are present in almost any organization of size. IT help desks are tasked with being first-line responders for information technology needs inside of an organization or for customers of an IT product or service.
While many IT help desk support tickets will have little to do with cyber security in and of themselves, IT help desk workers in a prime position to both implement cyber security policy and educate workers about cyber security. Many IT help desk employees find their way into cyber security with a little additional training. That makes this position one of the best choices for those currently in school for cyber security, right out of school, or thinking about a cyber security education.
Network administrators occupy a continuum of positions from not very cyber security-centered roles all the way to security administrator roles. With that said, any network administrator worth their salt should take information assurance objectives into account when conceptualizing, configuring, and maintaining networking devices and topographies.
Network adminstrators work for organizations of all sizes and are tasked with being the “go to” networking professional for the creation of, optimization of, and maintenance of networking technologies. While there may not be a great deal of cyber security verbiage in some network administrator job descriptions, there are security implications for most networking choices.
Network administrator jobs can be earned with an associates degree or above in information technology-related fields, as well as through professional certifications such as the Network+ exam. Once you’ve established yourself as a Network administrator, cyber security-related tasks will likely be part of your day-to-day routine. With more practice and potentially a degree in cyber security, you can advance to even more cyber security-centered roles.
Systems administrators fill a role similar to network administrators, though centered around end-user utilized software and hardware. Similarly to network administrators, some systems administrator job descriptions may not contain much mention of cyber security. But most systems administrator tasks have a range of repercussions related to cyber security.
Simply configuring a new user’s computer can involve shutting down unused ports, giving the user proper permissions to access or change files, and configuring VPNs or firewalls. These same types of choices may be available for nearly every device or piece of software configured. In this sense many systems administrators are at the heart of implementing a sound cyber security protocol. And for this reason they are a great position to gain practical knowledge of cyber security through before jumping into a more cyber security-centered career.
Engineering and Maintenance
Engineering and cyber security maintenance comprise one of the three major categories of cyber security “in the wild.” Short of responding to a live “incident,” or establishing cyber security policies, a great deal of cyber security is accomplished through these technical positions in cyber security engineering and maintenance.
Below we’ve listed all of our in-depth guides on cyber security engineering and maintenance positions. Many of these positions are quite lucrative, in high-demand, and many can be entered with just an associates or bachelors degree.
- Security Architect Job Facts and Figures
- Security Engineer Job Facts and Figures
- Security Consultant Job Facts and Figures
- Cryptographer Job Facts and Figures
- Security Software Developer Job Facts and Figures
- Security Administrator Job Facts and Figures
- Security Source Code Auditor Job Facts and Figures
To run through some of the most popular engineering and maintenance careers within cyber security, let’s start with security engineer positions.
Security engineers are at the heart of optimizing any software, hardware, or IT service with cyber security practices. Some teams may employ a single security-centered engineer, while others may be comprised of only cyber security engineers led by a project manager or security architect.
A common job description for a security engineer is centered around a product lifecycle. From the beginning of a new product, cyber security decisions should be built in to ensure the best security outcomes.
Tasks that security engineers may perform throughout a product lifecycle include:
- Performing vulnerability tests
- Performing risk analysis
- Documenting risks and responses
- Providing training to others on engineering or user staffs
- Building of firewalls, anti-virus software, and mending systems for an organization
- Testing of organization infrastructure for cyber security risks
- Communicating risks to proper team members or other teams
As security engineers are often both skilled engineers that also have chops in cyber security, demand for talent is quite high. The average salary for security engineers is $105,527, with top earners making closer to $150,000 a year.
Security Administrator roles roles often perform many of the tasks network and systems adminsitrators do, but with a focus on security. These administrators may help to set up an individual computer, configure routing technologies, research and install new firewalls, and configure VPNs. Additionally, security administrators often provide policy recommendations regarding cyber security. Or, in small organizations, are in charge of coming up with the entire cyber security protocol set.
Additional job duties of security administrators include fending off intrusions, educating team members about cyber security, and creating and updating disaster continuity plans. In small organizations, security administrators may be the sole dedicated cyber security professionals. In larger organizations, they may work alongside a team of security administrators or within a more interdisciplinary team.
Security administration is a great route through which to segue into cyber security from network or systems administration (or a great place to start after a cyber security degree). Demand is high for security administrators, who make an average salary of $77,250.
Security Architects are at the center of most large cyber security departments or product development cycles. The term ‘architect’ in this case, generally means a worker with in-depth knowledge of all systems surrounding those being worked on. Security architects are experts at working with the cyber security infrastructure employed in an organization. They often lead teams of other cyber security engineers and are the go-to technical resource for important projects.
Additional duties of security architects include planning the delivery of solutions, mentoring team members, setting cyber security policy for entire organizations, developing requirements for new IT infrastructure, implementing test scripts to verify system integrity, staying up-to-date with emerging cyber security trends, and more. Security architects are in high demand, and this job can be quite demanding. Security architects make an average of $145,770, with the top 10% of earners making over $200,000 a year.
Incident Response
No matter how well secured your environment, there will come a time when a cyber security incident surfaces. Perhaps an employee unwisely provides information to an anonymous phone call. Perhaps one of your vendors is comprimised. Or perhaps a rival corporation unleashes a distributed denial of service attack to attempt to take down your services.
Whatever the situation, having a quality incident response team (in the office or as an external service) can make the difference between your business shuttering its operation, and a minor inconvenience.
We’ve covered a wide range of careers here at CyberSecurityDegrees, including those in incident response. We’ve crafted guides for a range of these careers listed below. Or scroll down to see some of the most popular incident response career descriptions:
- Incident Responder Job Facts and Figures
- Security Consultant Job Facts and Figures
- Security Administrator Job Facts and Figures
- Security Specialist Job Facts and Figures
Incident responders are tasked with preparation for, live response, and reporting after a cyber security incident. Those that excel in incident response often possess the ability to work well under pressure, communicate clearly, advanced planning skills, and a number of technical chops.
Job responsibilities for incident responders may include setting plans in place to recognize system and network vulnerabilities, developing a plan of action in the case of different emergency types, oversee monitoring for suspicious activity, running penetration tests and security audits, and providing detailed incident reports when an incident does occur.
While a whole chain of command often exists in incident response teams, entry to mid-level incident responders have an average salary of $52,160. This number rises over $100,000 a year as members rise through the incident response team.
Security consultants are often seasoned cyber security veterans who start their own firm or work for a third-party consulting firm. Consultants provide another “pair of eyes” and present fresh ideas to organizations that already have dedicated cyber security teams, or who have no dedicated cyber security members.
While many security consultants do specialize as time goes on — for example, in network intrusion detection, or penetration testing, or internet of things devices — they are generally well versed in a broad range of cyber security skillsets.
Typical jobs for cyber security consultants may include auditing the current information systems security within an organization, penetration testing (or ethical hacking), reviewing policies related to cyber security for another organization, appearing as expert witnesses in court, or giving their own interpretation of incident reports.
Many cyber security consultants run their own firm, so earning can get quite high. With that said, the average cyber security consultant salary in the United States is $73,000.
Policy and Forensics
A host of cyber security jobs aren’t centered around engineering or immediate incident response so much as more general policy concerns. These jobs include law enforcement community use of cyber security methods, those in charge of computer forensics, and those in charge of pressing issues like privacy and compliance.
We’ve listed our in-depth guides to policy and forensics careers below. Keep on scrolling for a brief overview of some of the most common jobs in this space.
- Security Analyst Job Facts and Figures
- Vulnerability Assessor Job Facts and Figures
- Security Consultant Job Facts and Figures
- Forensics Expert Job Facts and Figures
- Security Source Code Auditor Job Facts and Figures
- Penetration Tester Job Facts and Figures
- Security Auditor Job Facts and Figures
- Ethical Hacker Job Facts and Figures
Directors of privacy are a relatively new role within many organizations that has been of increasing importance with the amount of consumer data retained (and lost in breaches). As the legal and public perception liabilities of mishandling consumer data have increased, so too has the importance of roles like director of privacy.
Generally speaking, directors of privacy will hold an advanced degree in information technology, management information systems, cyber security, or business. These positions are often placed in-line with that of vice president-level positions within an organization. As such, one can expect to be fully accountable for the handling of all privacy related issues within an organization.
Commensurate with the level of responsibility held by directors of privacy, earnings can be quite strong. The average salary for directors of salary is $147,000, with the top 10% of earners making over $180,000.
Forensics expert positions related to cyber security exist in a wide range of governmental agencies, third-party cyber security consulting firms, and within corporations. Forensics in a cyber security context is the application of methods related to auditing a past cyber action or investigating a cyber asset. This can take the form of tracking down details on a cyber assailant, reconfiguring data that was hastily wiped to cover up a bad actor, or generally investigating a cyber crime.
As the number of cyber exploits increases exponentially, demand for cyber security-related forensics experts is also growing. The average salary for forensics experts in the United States is $95,510, with the top 10% of earners making over $150,000 a year.
While also part of engineering teams, security source code auditors also play a role in forensics and overall governance and compliance among information technology companies. Security source code auditors perform a hybrid role centered around investigating individual lines of code within information technology services.
Security source code auditors are generally well versed in overall security design concepts, auditing methodologies, software development, and criminal justice. Those that excel generally have great attention to detail, can work independently and are good at explaining their technical findings to non-technical team members.
As with many specialized cyber security positions, security source code auditors are in high demand. The average salary for this role in the United States is $77,853, with top earners making closer to $100,000 a year.
Director of compliance are increasingly common, and growth is driven by many of the same reasons as director of security positions. As data breaches have become more high profile and common, regulatory bodies have stepped in to try to control organizational use of data.
While regulatory oversight often enables consumer protections and makes for a ‘better’ product, for many organizations lack of compliance is a liability. When dealing with bodies that have the power to shutter the doors of your business, ensuring that regulations are met is paramount. And thus entire teams are often dedicated to compliance in larger organizations.
Duties of director of compliance positions include establishing roadmaps for making organizational changes that meet compliance, negotiating with stakeholders and regulatory bodies, educating team members, enacting compliant policies for branches of the company, risk analysis, and staying up-to-date on trends in compliance.
The average salary for directors of compliance in the United States is currently $171,836. The highest ten percent of earners in this role bring in over $200,000 a year.
Upper Management
In the past, cyber security within organizations was relegated to one or a handful of administrator position(s). Today, many organizations have an entire department devoted to cyber security, or even focus on offering cyber security products as their main offering.
As with any organizational component that grows in scale, effective leadership becomes one of the main contributors to the unit’s success. Cyber security is no different. Except for the fact that in a discipline so multifaceted, many employers find it hard to find those with both all the prerequisite skillsets and leadership qualities.
That’s where the right candidate can truly excel. While there’s a massive shortage of general cyber security workers, there’s an even bigger shortage of skilled management within cyber security. For the right type of candidate, pursuing a managerial career in cyber security can be the opportunity of a lifetime.
Below we’ve listed some of our career guides on management-level positions within cyber security. For a brief overview of some of the most common managerial positions, scroll below.
- Chief Information Security Officer Job Facts and Figures
- Security Director Job Facts and Figures
- Information Security Manager Job Facts and Figures
Information security manager jobs typically function at the project or program manager level, though unlike managerial roles in other fields, the product or program being produced relates to cyber security. Typical job responsibilities of information security managers include taking responsibility for the development, testing, and improvement of information security systems, mentoring of team members, hiring and firing, and being able to act a liaison between technical team members and a variety of stakeholders.
Given the range of tasks for which information security managers are responsible, as well as the growing importance of cyber security within many organizations, salaries are good for infoSec managers. The average salary for an information security manager in the United States is currently $119,915 a year. This salary rises to over $160,000 a year for the top 10% of earners.
Finally, chief information security officers (known by the acronym CISO) are the highest level of management within many cyber security organizations. Reporting directly to the CEO, CISOs are responsible for the execution and future proofing of all cyber security activities within an organization.
This role can involve a large amount of work related to consumer privacy, regulatory compliance, overseeing cyber security research, or overseeing technical matters such as developing a new cyber security product. As the final say on cyber security operations, future-proofing, and incident handling, it’s no wonder many CISOs are well compensated
The average salary for chief information security officer roles in the United States is $204,000. The top 10% of earners in this role earn over $400,000 a year.





