75+ Shocking Facts on Cyber Security
While the late twenty-teens aren’t yet a literal Brave New World, our newly-connected lives do inhabit a space requiring new forms of bravery, expertise, and common sense. The modern internet is less than a decade old. And our progressively-long digital trails, growing collection of connected devices, and exponentially-increasing range of digital services have placed many on a frontier few have much experience managing. Just following the news, it’s clear that even many large and otherwise esteemed organizations are proceeding off the cuff in terms of methods of cyber defense. In many ways, that’s all they can do. The demands of simply making a product work are often high. Meanwhile, the cost effectiveness (and simple effectiveness) of cyber crime has never been higher. While some of the facts below are over 30 years old, and from the foundation of the field of cyber security, many facts below describe criminal tactics employed thousands of times a day. This isn’t said as a reason for despair. But rather to highlight the shock and wonder incited by the inventiveness employed and scale of our new digital battlefields. Check out 75+ of the most shocking facts on cyber security below:
On This Page:
Economic Impact:

(Source)
- 1.In 2016, cyber incidents cost the global economy more than $450 billion. That’s a huge number, and for context here are some comparisons. That means that in 2016 more than twice as much money was lost in cyber incidents as was brought in by auto sales worldwide. For doomsayers, that’s almost twice as much as the annual interest on the United State’s debt. It’s also four times the amount that the U.S.’s discretionary federal education budget it!
- 2.While large U.S. firms are the best prepared for cyber attacks in the world on a per-country basis, 51% of large American firms are still rated as unprepared by experts. This is much better than large German firms, however, who make up 39% of the worst-prepared large firms in the world. With this said, large U.S. firms are by far the most targeted firms in the world, meaning even solid preparations will not always be able to repel cyber attacks.
- 3.Corresponding with the massive challenge to secure our newly-connected world is the projected major growth of cyber security industries. While the cyber security market was valued at $137 billion at the start of 2017, the market is projected to grow to $231 billion by the start of 2022, almost doubling in size!
- 4.Cyber security market opportunities also extend to the individual level, with over 1 million cyber security job openings in 2016 and 2017. CSO Online notes that many U.S. students graduate from top computer science programs with little or no information assurance curriculum. While there is more than one job for every cyber security graduate, many graduates won’t directly move into more senior positions (of which there are many, many openings). Potentially the most alarming part of the cyber security skills gap are for positions more senior than information assurance analysts. (Information assurance analysts often monitor screens filled with security-related readings to assess for compromised systems. More senior positions are often the cyber security workers who actually work out the strategies for repelling cyber attacks.)
- 5.By 2019, Cisco estimates that there could be 1.5 million empty cyber security jobs. You may ask, why so many? In part, because cyber attacks are some of the most cost effective and low risk forms of crime. Also, unlike more traditional criminal activity, great portions of cyber crime can be automated. Check out our bot section for more info.
- 6.As of late 2016, more than 4,000 notable cyber attacks occurred per day. In recent years, the increase in cyber attacks has been exponential. The fallout of cyber attacks has also been more serious, as the rise of cyber attacks has coincided with increasingly large amounts of sensitive information kept online and in computer systems. 2016 saw a 300% increase in cyber attacks just from 2015, and 2017 have proven to up the ante yet again. For a look at live cyber attacks (just a portion, really), check out this cyber attack map by Norse. Holy cow.
Hacktivism:
- 7.Hacktivism is defined as the subversive use of computers and systems to promote a political agenda or social change. Unfortunately, hacktivism is often outside of the law, and at times comes across as completely misguided vigilantism. The term was first coined by Cult of the Dead Cow member “Omega” in 1994. With that said, the definition of hacktivism is somewhat ambiguous, with acts of hacktivism being labeled both cyber terrorism and activism.
- 8.One of the most productive instances of hacktivism can be found through the Freenet peer-to-peer communication engine. Freenet offers a suite of software for publishing and online communications without fear of censorship. In a day and age in which social media does take stances against out-of-fashion political though, Freenet offers anonymity and decentralized data networks that allow users to speak their mind without fear of content being taken down.
- 9.Common techniques of hacktivists include the defacing of government and organizational websites, doxing of individuals that hacktivists disagree with, and enacting DoS attacks against organizations they don’t agree with the values of. Techniques more directly tied to “ground up” social change include geo-bombing, in which large numbers of images or videos are posted geotagged to Google Earch, the mirroring of websites that have taken down content, and advancing secure channels through which to leak information about potentially corrupt entities.
- 10.One of the more humor-driven (read, trolling) hacktivist groups is Lulz Security (Lulzsec). Lulzsec did not appear to be a group motivated by financial profit, but rather in the ‘fun of creating mayhem.’ During a 50 day run in 2011, LulzSec defaced and leaked many confidential documents from a number of large organizations including Fox, Sony, the CIA, PBS, and the FBI (among others). Cheered on by an audience of tens of thousands of Twitter followers, LulzSec promoted their hacks with witty names like ‘F*** the FBI Friday.’ On the political front, LulzSec seemed interested in combating the role of the government and large corporations in censoring the internet.
- 11.WikiLeaks are probably the most socially-endorsed hacktivists (depending on who you ask). Wikileaks was founded in 2006 by Australian internet rights activist Julian Assange, and in the 11 years since it’s creation has amassed some 10 million classified documents leaked to the public. Though Assange has lived in the Ecuadorian embassy for several years, and would likely be arrested if he were to leave, press organizations worldwide have hailed Wikileaks’ efforts in the name of government transparency and anti-corruption. Early documents and footage released included detailed documentation of U.S. expenses during the War in Afghanistan, footage of Iraqi journalists being bombed, and diplomatic cables sent by the U.S. State Department.
- 12.UGNazi — another hacktivist collective — are well known for their staunch opposition to the CISPA and SOPA bills. CISPA and SOPA were perceived by many critics and the UGNazis as eroding privacy and first amendment rights online. Favored tactics by the UGNazis include denial of service attacks against departments of the US government in retaliation. Other attacks have included defacing and DDoS attacks against Six Flags, 4Chan, Twitter, HostGator, WePay, the Wounded Warrior Project, and Westboro Baptist Church. Several members of the group, then teenagers, have been identified and prosecuted for their roles in the collective.
Malware:

(Source)
- 13.The term “Malware” is short for “malicious software”. Malware is one of the most general categories describing types of cyber attacks and includes viruses, spyware, rootkits, worms, trojans, and more.
- 14.Predictably, malware has grown in sophistication and scale in recent years. Traditionally anti-malware software identifies malware based on a digital signature. The rise of “polymorphic malware” in recent years has led to new difficulties in identifying and preventing malware. Polymorphic malware is code engineered to adjust it’s digital signature every time it executes. This allows malware to evade discovery for longer, infect more computer systems, and generally wreak havoc to a greater degree. Today, largely thanks to a growing number of cyber criminal players as well as polymorphic malware, 94% of malware is unique.
- 15.Annual counts of new unique forms of malware seem to ebb and flow in a predictable way. According to the McAfee Quarterly Malware Report from April of 2017 the last few years have exhibited a larger number of new malware types in the fourth and first quarters of the year, with the number of new malware strains ebbing from quarters two to three. This could be related to increased opportunities for gathering personal financial data around the spending-heavy holiday season. Also, the number of new connected devices released around the holidays is usually higher.
- 16.Mobile malware accounts for a relatively small portion of total malware at 15M out of 600M+ total types of malware. With that said, mobile malware’s growth rate is much higher than that of all malware. From Q4 of 2015 to Q4 of 2016 the number of total mobile malware strains almost doubled from 8M to 15M+.
- 17.There are large regional variances in malware infection rates. Looking at mobile malware infection rates by region, Asia has by far the highest number of users reporting malware infection (at 12%). Europe has the lowest percentage of reported mobile malware infection at slightly over 4%, while North America has a mobile malware infection rate of slightly over 6%.
- 18.Traditionally computers running windows have been much more susceptible to malware. This is partially due to a prevalence of zero-day vulnerabilities in Windows as well as increased focus on Windows by cyber criminals due to the prevalence of large corporations using the operating system. The fourth quarter of 2016, however, saw the largest leap in new malware affecting iOS in the history of the operating system. Between Q3 and Q4 of 2016 the total number of malware strains affecting iOS devices jumped from roughly 140,000 to over 450,000. This jump was largely accounted for by adware bundled in software not acquired from trusted developers in the Mac App Store.
- 19.Potentially due to the American presidential elections, the sector most affected by Malware in Q4 of 2016 was the public sector (largely voting fraud and defacing attacks). Simultaneously, China and the Philippines engaged in a number of major cyber attacks over the South China Sea in this period. The public sector experienced close to 180 major malware incidents worldwide in this 3 month period. In descending order, other affected sectors included single individuals, health care, online services, and finance.
- 20.The growth rate of new phishing and spam URLs has decreased through 2016 from an all-time high in 2015. This could be due to increasingly sophisticated scanning in emails, social media links, and increased browser security.
- 21.The top network attacks of 2016 (in descending order) included SSL attacks, DoS attacks, Worms, Brute Force Attacks, Browser Attacks, Botnet Attacks, and Scan Attacks. By far the largest single nations hosting botnet control servers are the United States (38% of botnet control servers), Germany (11% of botnet control services), and the Netherlands (6% of botnet control services)
Spyware:

(Source)
- 22.Spyware, as one might expect, is a class of software with the aim of gathering information on a user without their knowledge. While many forms of spyware are legitimate malware, the tracking of users is also increasingly part of genuine software and web services that view user data as valuable. The most common forms of spyware (malicious and otherwise) include adware, systems monitors, tracking cookies, trojans, and keyloggers (as are found on many corporate or public computers).
- 23.Spyware often spreads bundled to intentionally downloaded software similar to adware or relying on phishing links or malicious sites. Common malicious spyware can be very hard to detect, and lead to system-wide consequences that exhibit closer to hardware malfunction that typical malware: internet connectivity issues, lack of typical CPU power, or crashing browsers. Common malicious spyware may use keyloggers during browser use, transmitting screenshots of what pages certain key strokes were entered on. As you can probably image, this is more than a privacy matter, and can lead to loss of valuable personal and financial information.
- 24.Components of software services that can loosely be termed spyware are often created by legitimate providers. Depending on one’s beliefs on internet privacy, this sort of spyware can be seen as either enabling better user experience online, or a blatant overstep by many popular web-based services and hardware providers. A 2011 report on the Wall Street Video (and corresponding video by CNET) detailed the fact that social media networks often track user activity far beyond the confines of the social media platform. When users are logged into social media accounts, interactions enabled through social media login data around the web often transmit data back to the social media provider. Over time, this leads to in-depth profiles on what user interests, demographics, and personal information from around the web.
Viruses:

(Source)
- 25.The first documented virus was created (in theory) in 1949 by John von Neumann, a lecturer at the University of Illinois. He describes the core components of most modern viruses in his essay “Theory of self-reproducing automata.” This work was expanded on in 1972 by German researcher Veith Risak. In Risak’s work, he postulated that computer programs can work in some ways similarly to biological viruses.
- 26.Michael Crichton’s 1973 sci-fi movie (now an HBO show) WestWorld made one of the earliest popular culture references to computer viruses. The movie, in which androids play as actors in a hyper-realistic wild west theme park starts to experience anomalous (and sometimes dangerous) behavior from the androids. On character summarizes the anomalies as ” a clear pattern here which suggests an analogy to an infectious disease process, spreading from one…area to the next.”
- 27.There are effectively two criteria for a piece of code to be called a virus. First, the piece of code must execute itself, often placing itself in the execution path of another file or process. Secondly, the virus spreads by replicating itself in some form. A common example of this occurs when a program replaces an uninfected file on a computer with a file hosting part or all of of the infection. Viruses may affect desktops, laptops, servers, and mobile devices.
- 28.While there were over a million documented types of viruses as of 2008, this is but a small fraction of the number of other cyber threats. Over 27,000 new malware strains are located per day, with over 75% of this malware being in the form of Trojans. Viruses just account for around 8% of the new strains of Malware.
- 29.Though effectively non-existent, early experiments with viruses noted that there is no such as a ‘benevolent’ virus. As part of the definition of a virus is that it makes unauthorized changes to a users computer. This notion has been challenged over time, however, as an invasive, self-executing piece of code could theoretically initiate a helpful procedure (say, defragmenting a disk, closing security vulnerabilities, or backing up files).
Worms:
(Source)
- 30.At their simplest, worms are malicious code that are able to self-replicate. Worms often achieve self replication by utilizing security loopholes in networks. Unlike viruses, which almost always corrupt or modify files on the target computer in some way, worms alone often largely affect the networks by which they travel through consuming bandwidth or other unintended consequences. With that said, worms are often bundled with other forms of malware with the term worm used to describe the fact that a bundle of malware can replicate itself and move from one system to another.
- 31.The first major worm (second overall) was created in 1988 by then graduate student Robert Morris. Unleashed from MIT’s computer labs, the worm was — according to Morris — not meant to be malicious, but rather to try to gauge the size of the internet. The code might have run un-maliciously, if not for a bug that allowed it to infect already infected computers again and again, slowing the computer down with each subsequent infection until it was un-usable. The worm affected what was estimated to be about 10% of the internet at the time. The Government Accountability Office estimated (in a supposedly wild case of guesswork) that the damages from the worm were in the range of $100,000-$10,000,000. This led to Morris being the first person prosecuted by the Computer Fraud and Abuse Act. Morris would go on, however, to become a computer science professor at MIT.
- 32.The first of all worms was potentially crafted with more malicious intent than the Morris Worm and was known as Jerusalem. This worm — also known as Black Box, because of the black box displayed during its initialization — would infect and bloat the size of every file running on a MS-DOS computer except for Command.Com. Particularly with the hardware of the day, this massively slowed down infected computers. Furthermore, Jerusalem would delete every program executed on Friday the 13th. Jerusalem inspired a host of malware that replicated the bloat and arbitrary deletions of programs in following years. While many later variants of Jerusalem were actually just viruses, early version included a bug causing the malicious code to re-infect systems over and over, effectively self-replicating. These early variants often resulted in all system memory being used up by increasingly bloated system files.
- 33.Since the creation of the first worms, there have been attempts to spread worms of good intent, though in practice even “beneficial” worms have led to unforeseen consequences on networks and considerable network traffic. One example of a worm made with good intent is the Nachi family of worms. The Nachi worms were spread through the early 2000’s and utilized vulnerabilities in Windows to enter into machines and install security patches to prevent future utilization of those vulnerabilities. Nachi worms were programmed to self remove on January 1, 2004, or 120 days after when they processed, whichever came first.
- 34.One of the most detrimental pieces of malware spread through a worm came in the form of the early 2000’s “ILOVEYOU” worm. This worm relied on some social engineering as it was sent through phishing emails with an attachment titled “LOVE-LETTER-FOR-YOU.txt.vbs” (a visual basic file slightly disguised as a text document). The worm was further aided by a setting hiding file attachment extensions in Outlook at the time. Unwitting users who opened the attachment would find a worm able to send itself to all of the user’s Outlook email contacts while overwriting files on the victim’s machine. The worm spread to tens of millions of machines on or before May 5, 2000.
Trojans:
(Source)
- 35.Trojans are pieces of malicious code that rely on social engineering to find placement, just like the original Trojan Horse. While they often can’t self replicate (phew), they often provide a backdoor into the infected computer. Trojans are often transmitted through drive-by downloads or disguised as benign email attachments. Beware of the file types of email attachments (particularly those ending in .TXT.vbs).
- 36.As of 2008, Trojans were by far the most common form of Malware, with 15% of computers recruited as part of botnets that spread malware, and over 85% of malware total coming in the form of Trojans.
- 37.One of the most famous early Trojans (common around 2000) was sent in emails titled “ILoveYou.” Relying on the emotional response or interest of the recipient, the email held a Visual Basic script disguised as a text love letter titled “LOVE-LETTER-FOR-YOU.TXT.vbs”. By 2002, the ILoveYou Trojan was the most common form of malware and had infected over 3 million computers.
- 38.Many cyber exploits rely on social engineering, but some malware takes the social aspect farther through automation. A common malware affecting Skype and other messaging apps contacts everyone on a users contact list with a simple greeting. For users who respond to simple lines like “hi” or “how are you” a phishing link is sent. Introverts just can’t get a break, can they?
- 39.Relying on the ability to obtain a backdoor into computers, Trojans are one of the preferred delivery methods for Ransomware. Ransomeware is the practice of encrypting information on an infected computer and withholding the encryption key until money has been extorted from the user. Find more on ransomware in our ransomware section.
- 40.Trojans also are often in search of computing power. Many Trojans have been used to mine bitcoins on networks of infected computers. This makes sense as most Trojan uses since the days of MS-DOS have been to make money. More recently, Trojans have been included in Android Apps. Apps that appear to be memory greedy and cause performance issues may be mining bitcoin using the computing power of your device (ouch!).
- 41.In the end, Trojans are just a way of delivering code to a device through subterfuge. What the code does is entirely up to the author. There are even a few examples of benevolent Trojans. In 2015, a Trojan known as WiFatch circulated through the web infiltrating a large number of Wi-Fi routers. What did WiFatch do with those routers? It patched them and then prompted users to update their passwords on unsecured routers. This is one of the better known examples of what some would call “GoodWare.”
- 42.As mobile use has skyrocketed, the attention of Trojan makers has shifted, particularly to Android. One of the most sophisticated Android Trojans is called Triada. Triada is able to leverage access to the Zygote Process (the central process of the Android OS) to effectively take over devices in secret. The Zygote Process is used as the template for Android apps, and once Triada has access to the Zygote it can effectively become part of every app on your phone (sending texts, making calls, accessing key strokes, downloading ads, and so forth). When SMS verification is used for purchases online, Triada can hijack the incoming text to direct funds elsewhere. Furthermore, Triada lives in the RAM of infected systems, making it extremely hard to detect.
- 43.There are a wide range of well-documented Trojans, often labelled by their purpose. Some of the most common Trojan types include Backdoor Trojans (open a backdoor onto your system), Exploit Trojans (take advantage of a security vulnerability), Rootkit Trojans (meant to conceal malicious activity in the future), Trojan-Bankers (meant to steal banking info), Trojan-DDoS (meant to enlist your system to help maintain a DDoS attack), Trojan-Downloader (meant to download malicious files), Trojan-Droppers (meant to ‘drop’ malicious files on your system), Trojan-FakeAV (infiltrates your system as a fake antivirus program), Trojan-GameThief (steals gaming accounts), Trojan-IM (steals instant messaging contacts and logins), Trojan-Ransom (initiates ransomware), Trojan-SMS (enlists your device to send texts), Trojan-Spy (a backdoor to spy on your computer), and Trojan-Mailfinder (meant to find email contact addresses).
- 44.Trojans are used by the governments of several German-speaking countries, where they have a legal framework erected around their use. The use of Trojans by the German and Swiss governments to spy on computers is often called “GovWare.”
Internet-Based Bots:
(Source)
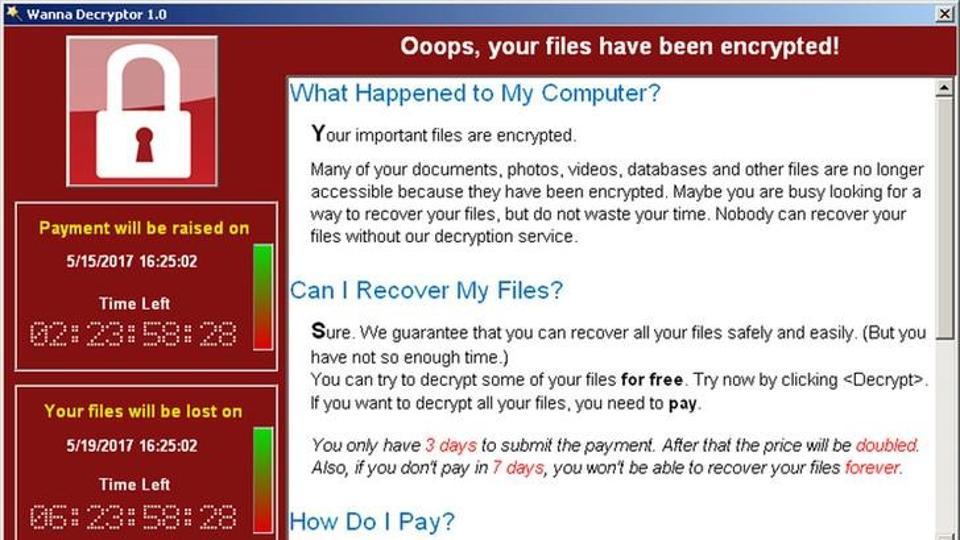
- 45.At their simplest, Bots are applications that run automated tasks over the internet. Bots have a wide variety of applications and generally excel at performing simple and structurally repetitive tasks much faster than human beings. Unsurprisingly, bot strengths can be used for good and bad purposes. Today, Bots are one of the most common delivery methods for malicious attacks online, with 92.5% of all websites having been the recipient of bot attacks. Botnets, or connected groups of infected systems doing the bidding of a malicious controller are a common method for delivering DDoS attacks, spam attacks, and mining bitcoin.
- 46.One innovative use of bots is to farm resources in MMORPG games such as World of Warcraft or Runescape. Many online communities that use in-game resources that are ‘farmed’ repetitively must provide some protection or screening processes for bots.
- 47.A common use of bots that advertisers are constantly seeking to screen and eliminate is the use of bots to raise visitor numbers for websites. One of the most high-profile cases of this occurred in 2012 when CNN iReporter reporter Chris Morrow had millions of pinged views removed from his content. It is unclear whether advertisers ever received their fraudulent payment back.
- 48.Though analytics services are constantly becoming more advanced at their detection of bots, in 2012 and 2013 it was estimated that 54% of display ads on sites internet-wide were never viewed by a human being.
- 49.Common precautions sites employ to minimize bot manipulation include the use of CAPTCHA phrases, labeling submit buttons on forms with unexpected text, “honeypot” pages that humans probably won’t visit with fake information (bots that scrape every page of a site might be fooled by honeypots), and limiting the number of attempts to access a page.
Doxing:

(Source)
- 50.Doxing is one of the most malicious forms of cyber attack. This attack type involves locating or deducing information about someone through online means in order to blackmail, generally inflict harm, or exact revenge on someone. Doxing is a common form of cyber bullying, “hacktivism,” vigilante justice, slander, underhanded reported, and internet mob rule.
- 51.Perhaps the most common initial methods of Doxing can be performed by almost anyone: using google and social media searches to find personal information that might have been published online. Your email address, phone number, physical address, or information on family members. Newer and more complex ways of doxing individuals are enabled through reverse image searches, using the WHOIS domain registry (if they own a website), searching through the white pages or government records, or using usernames of individuals (if that’s the Doxer’s starting place) to reverse look up the persons contact information.
- 52.Maltego is a proprietary software that ships with Linux and can be used for more advanced identity lookup. The software focuses on the modelling of relationships in open information sources. By automating data mining, tools like Maltego may be used to map locations worth investigating for personal information on those being Doxed such as professional relations, locations of work or liesure, hobbies, organizations or family members.
- 53.“Creepy” is an advanced geo-location tool that mass extracts location data from tweets and flickr feeds. Once aggregated, Creepy users can pin down the most common locations of those being Doxed, often home, work, or addresses of close relationships.
- 54.Particularly advanced Doxing methods may be carried out by malware, providing a large range of data through infected computer systems. Related to ransomeware attacks, this form of Doxing may involve blackmailing those who are attacked by making demands in exchange for the safety of gathered personal information.
- 55.Some of the most notable examples of Doxing occurred when Reddit vigilantes wrongly identified suspects of the Boston Marathon Bombing from a set of public photographs. The ensuing pressure online led to one of the wrongly identified — Sunil Tripathi — committing suicide. Another high-profile Doxing incident occurred when an anti-abortion site published a hit list of abortion doctors. 8 abortion-providing doctors were killed by anti-abortion terrorists using the information on this list from 1993-2016.
Social Engineering:

(Source)
- 56.Social engineering refers to a group of cyber attack tactics that rely on tricking humans into breaking security protocol. As are social engineering components to many large data breaches, social engineering is regularly cited as the most common cyber attack technique, particularly when talking about cyber attacks against large organizations.
- 57.Perhaps the most common form of social engineering is phishing. According to McAfee in 2017, a whopping 93% of social engineering attacks involve phishing. In phishing attacks, the attacker makes fraudulent claims, often claiming to be a legitimate entity or trusted source in an attempt to gain personal information or get people to install malicious software. Common techniques include getting people to click links in emails that lead to drive-by downloads and making charity pleas after natural disasters in order to get private information. Phishing has taken additional technologically-aided forms in recent years as well, including text phishing, phishing by phone, or navigating people to websites via mailed correspondence.
- 58.Spear phishing is a phishing technique that targets specific individuals whom the assailants have information about. Information is often taken from social media accounts or public information and used to make pleas seem more legitimate. One common technique is to pose as a friend from your social media. Assailants may know your name, address, occupation, hobbies, and so forth to be able to tailor their emails and try to scam you out of sensitive information.
- 59.Several forms of social engineering involve being in the same physical space as a assailant. If part of a cyber attack technique involves physically stealing information or planting malicious code onto otherwise secure systems, the assailant may try to “tailgate.” Tailgating occurs when someone physically follows you into a secure information. Potential prompts from the assailant may include asking you to hold the door open because the assailant has “forgotten their identification” or other related ploys.
- 60.Baiting is another social engineering technique that takes place in the physical location of the attack. This technique involves planting an infected USB, hard drive, or CD in the location to the attacked. The attack relies on the assumption that someone will load the storage device onto the system to see what it contains. With the proper settings, this is all the attacker needs to plant malware onto the system and gain backdoor access.
- 61.Pretexting has been behind a number of large scale attacks. In this type of attack, the attacker fabricates false circumstances often including their own identity in order to get an individual or someone within an organization to divulge sensitive information. Common techniques include asking someone for financial information to verify their identity, or pretending to be a coworker of someone asking for login information to a shared account. Multi-factor authorization is one of the more surefire ways to guard against pretexting. Pretexting is an extremely common form of cyber espionage used on large organizations. According to Verizon’s 2017 Data Breach Investigations Report 81% of breaches tracked involved comprimised login credentials.
Ransomware:
(Source)
- 62.Incidents of Ransomware have exploded since 2015. In ransomware attacks attackers freeze the screen of an infected system and threaten to either publish private data included on the system, or encrypt and never decrypt information on the system until payment is received. Ransomware is typically transferred as a Trojan, or a legitimate looking file that hides malicious code.
- 63.Along with mobile malware generally, ransomware has been one of the fastest growing cyber threats, jumping from roughly 2.8M known strains at the start of 2015 to over 9M known strains at the end of 2016.
- 64.As sophistication of Ransomware has increased, so too has the desperation of those attacked. This has led to extortionist (literally) increases in average ransoms paid to unlock computers. In 2015 the average ransom was $294, but in 2017 the average ransom has jumped to over $1,000. Talk about anti-malware software being a good deal!
- 65.There are two main types of Ransomware, the first involves freezing the screen of an infected computer in such a way that many who are not technically savvy often cannot unfreeze the screen. Historically, this has been the most prevalent form of ransomware. While not foolproof, a large enough percentage of those infected with this non-encrypted form of ransomware have paid to make the scame highly lucrative. A second, newer form of ransomware, encrypts the files on the infected computer.
- 66.While encrypted Ransomware has been openly known about since 2005, this form of malware returned to prominence in 2013 with the growth of the CryptoLocker attack. In this attack, many infected users were coerced into sending ransoms in the form of Bitcoin, thus preserving the anonymity of the attackers. In a 2 month period of late 2013, ZDNet estimates that the perpetrators of Ransomware bagged somewhere around $27 million.
Denial of Service Attacks:
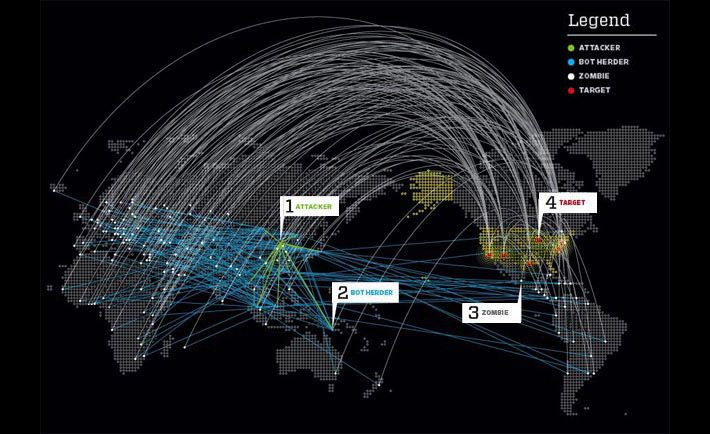
(Source)
- 67.Denial of Service Attacks (DoS) are commonly used by state actors, hacktivists, terrorists, in corporate cyber warfare, for revenge, for blackmail, and just by internet trolls. DoS attacks harm attacked entities by making online resources temporarily unavailable to the users of that resource. The most common method for performing DoS attacks is to flood the online resource with superfluous (or fake) requests, overloading the resources that are available to present an online service. In a Distributed Denial of Service attack, requests flood a resource or service from many different locations, making it harder to pin down and block fake traffic and requests.
- 68.As with almost every form of cyber attack, DDoS attacks have ramped up in frequency and severity over time. In 2016, the largest publically recorded DDoS attack was clocked at over a terabyte of fake requests a second. For scale, that’s roughly the equivalent of 85,000 users streaming high definition video. Of course, not that many individuals were involved with the attack which utilized botnets including 145,000 hacked digital cameras to deliver the attack from different locations. Few if any sites can actually handle that large of an influx of unexpected traffic, so you can imagine the affected sites went down immediately. The largest prior DDoS attack was hardly half the size of this 2016 attack.
- 69.Machines are often recruited to participate unknowingly in DDoS attacks through trojans and worms. Essentially all mobile, internet-connected, and internet of things devices can be harnessed for DDoS attacks, with many IoT devices and routers largely unsecured. Mobile devices hijacked for DDoS attacks may experience extremely slow loading times similar to mobile devices hijacked for the purposes of mining bitcoin.
- 70.HTTP Post DoS attacks were first discovered in 2009, and involve the sending of legitimate requests to a server while limiting the request transfer to an extremely slow transfer rate (say, 1 byte/110 seconds). By opening up many requests that do not close for some time, this type of attack can use up every available connection to the server for some time.
- 71.DDoS extortion has grown increasingly prevalent in attacks on financial institutions. A number of high profile attacks on Paypal and large banks have yielded demands from attackers, saying they will drop the attack if a payment of a certain amount is sent.
- 72.Degradation of service attacks involve long-term attacks that “pulse,” sleeping for a time and then flooding service providers. Predictable this type of attack may not completely derail a service provider or site, but rather degrade their service offerings over the long run.
Zero-Day Vulnerabilities:
(Source)
- 73.Zero-day vulnerabilities are holes in existing software that software makers do not yet know are there. “Zero day” refers to the unknown nature of the vulnerability when it is first uncovered by developers or the community who use the software. Once a zero-day vulnerability is uncovered, a race begins between the developer of the software and the hackers. While the hackers often try to get the most malicious use out of the vulnerability while the developer tries to secure the vulnerability as soon as possible.
- 74.A zero-day vulnerability for sale was uncovered in 2016, being sold on the dark web by a Russian cyber criminal ‘BuggiCorp.’ The zero-day vulnerability was believed to be able to affect machines running Windows from Windows 2000 to Windows 10 by allowing any user to gain administrative access. With over 1.5 billion Windows users worldwide, the vulnerability’s price of $90,000 on the dark web is quite paltry. While it was unclear whether or not the exploit was purchased, ‘BuggiCorp’ shared two videos of the exploit working. One video was after a major Windows security update, leaving open the possibility that the exploit could be used to deliver mass amounts of malicious code in the future.
Scareware:
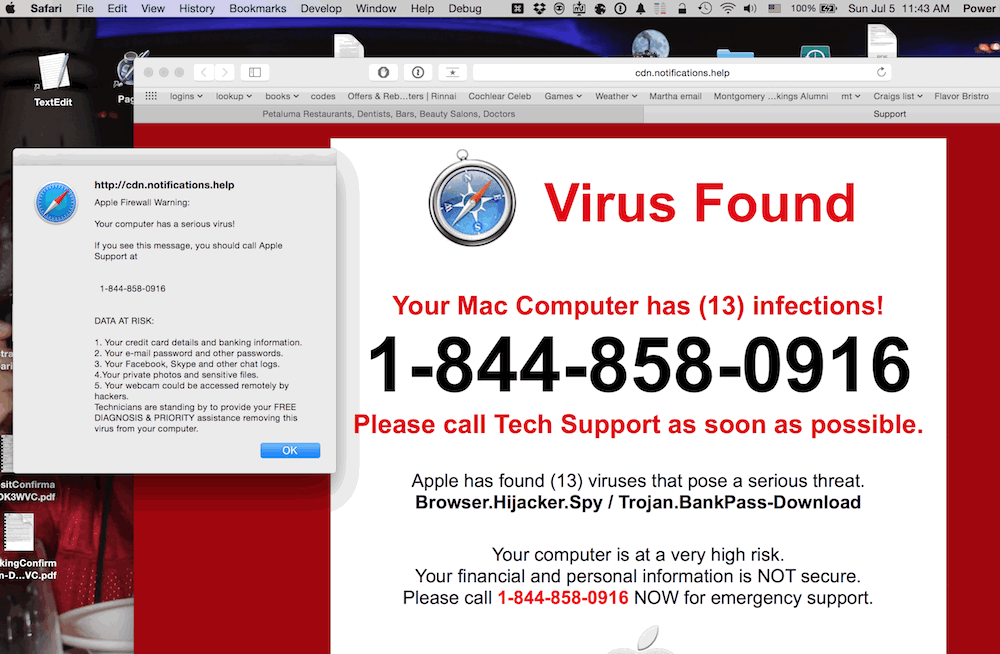
(Source)
- 75.Scareware is a class of malware that incorporates social engineering (largely phishing), trojan horses, and ransomware tactics to manipulate users using fear, anxiety, or perception of threat. Often lumped into other categories of cyber threats including malicious websites, email phishing, trojans, spyware, or adware, scareware is more a descriptor of the emotive focus of the attacks than the specific method through which the cyber attack takes place. Common scareware techniques involve the the infection of systems or browsers resulting in repetitive warnings or threat notices. Generally these notices are accompanied by a product for download such as a fake anti-virus software, a fake commercial firewall, or a fake registry cleaner. Some scareware would help cyber criminals profit through the sales of these products, others would result in demanded ransoms, while others yet were used for pranks or simply to damage systems.
- 76.The height of scareware “scares” was in 2009-11, when cyber criminals managed to infect some 1.5 million sites so as to present unauthorized popups that when clicked would lead to scareware initialization. Scareware has persisted in some forms, however, and grown more sophisticated in many ways. Scareware presented through popups will often mimic the styling of your native operating system to promote legitimacy and attempt to get viewers to provide the initial drive-by download. The best ways to avoid scareware include the purchasing of legitimate internet security tools and avoiding illegitimate applications that come bundled with adware.