50 Online Tools Every Cyber Security Professional Should Know About
There a notion in cyber security that the job of a cyber aggressor is much easier than that of a cyber security professional. Cyber assailants just need to get right once to wreak havoc on the systems and devices within a defending network. A defending network has to get security right 100% of the time to remain secure. With the range of newly connected devices growing exponentially (think tracking beacons, refrigerators, and even stop lights), there are more potential vulnerabilities than ever. Cyber security professionals are only human (for now), so the mantra has truly become how do cyber security professionals work smarter, rather than harder. One key element in this equation is that of the tools available to cyber security workers. While there are certainly scores more cyber security tools than we’ve included on this list, a vast majority of cyber security analysis and monitoring tasks can be performed with the tools below. Besides using most of the tools ourselves, we’ve scoured the internet to find the most widely used and supported tools. This is important as when you have questions about the effective use of a tool below (and you will), you’ll want to reach out to communities that are actively implementing this tool in production environments. While a number of the tools below effectively fall into multiple categories, for the sake of browsing we’ve broken the tools into the following primary categories.Jump To:
- Tools for Hardening Networks
- Tools to Secure Emails
- Tools for Internet Security
- Tools for Auditing of Networks and Networking
- Tools for SIEM
- Tools for Scanning Vulnerabilities
- Tools for Penetration Testing
- Tools for Breach Alarms
- Tools for Management and Attacking of Passwords
- Tools for Encryption
- Suites of Tools or Cyber Security Frameworks
- Tools for Cyber Security Reconnaissance
- Tools for Learning Cyber Security Tools and Concepts
Tools for Network Hardening
TCPCrypt
 TCPCrypt is one of the most popular and accessible “opportunistic encryption” solutions. With little to no configuration or customization, TCPCrypt seeks to encrypt all of your network traffic. In the event that an endpoint is not properly configured for encryption, TCPCrypt gracefully falls back on TCP communications. While not as strong as VPNS or other custom encryption solutions, TCPCrypt is more realistic for many settings in which a wide variety of assets need their traffic secured quickly and with no work from each end user.
TCPCrypt is one of the most popular and accessible “opportunistic encryption” solutions. With little to no configuration or customization, TCPCrypt seeks to encrypt all of your network traffic. In the event that an endpoint is not properly configured for encryption, TCPCrypt gracefully falls back on TCP communications. While not as strong as VPNS or other custom encryption solutions, TCPCrypt is more realistic for many settings in which a wide variety of assets need their traffic secured quickly and with no work from each end user.
Argus
 Argus is a free, open source network traffic analyzer. The name Argus stands for Audit Record Generation and Utilization System and works on most major operating systems and server configurations. Common tasks performed by Argus include analyzing data packets as well as entire data streams. Comprehensive reporting and fast data processing are additional perks of Argus.
Argus is a free, open source network traffic analyzer. The name Argus stands for Audit Record Generation and Utilization System and works on most major operating systems and server configurations. Common tasks performed by Argus include analyzing data packets as well as entire data streams. Comprehensive reporting and fast data processing are additional perks of Argus.
PacketFence
 PacketFence is an open source (and entirely free) Network Access Control solution. This tool is widely used in more than 5,000 large corporate and public settings. The list of features of this NAC manager include being able to perform role-centered access control on networks or any size, the ability to segment off troublesome layer 2 devices, bring your own device support, compliance checks, and malware removal.
PacketFence is an open source (and entirely free) Network Access Control solution. This tool is widely used in more than 5,000 large corporate and public settings. The list of features of this NAC manager include being able to perform role-centered access control on networks or any size, the ability to segment off troublesome layer 2 devices, bring your own device support, compliance checks, and malware removal.
WireShark
 Wireshark is perhaps the most widely used protocol analyzer. Wireshark runs on all of the most widely used platforms and OS’s. It can live print data packets from a variety of security protocols, and even has built in decryption. An intuitive GUI allows users to color code packets meeting certain criteria.
Wireshark is perhaps the most widely used protocol analyzer. Wireshark runs on all of the most widely used platforms and OS’s. It can live print data packets from a variety of security protocols, and even has built in decryption. An intuitive GUI allows users to color code packets meeting certain criteria.
SecurityIQ PhishSim
 The InfoSec Institute has a wide product line that focuses on cyber security training for organizations. After all, one of the most vulnerable aspects of any network (perhaps the most vulnerable) is human error. SecurityIQ’s PhishSim has 1000’s of pre-built phishing email templates that are added to every week. The software comes with the ability to analyze results and send emails of a variety of “difficulty” levels to test your team mates ability to detect phishing attacks.
The InfoSec Institute has a wide product line that focuses on cyber security training for organizations. After all, one of the most vulnerable aspects of any network (perhaps the most vulnerable) is human error. SecurityIQ’s PhishSim has 1000’s of pre-built phishing email templates that are added to every week. The software comes with the ability to analyze results and send emails of a variety of “difficulty” levels to test your team mates ability to detect phishing attacks.
Tools for Securing Emails
Lucy
 Lucy is a great alternative to PhishSim (above) that goes above and beyond simply securing emails. With a free community version, this tool can be run from a web application or a Debian install. This platform helps to automate the sending of mock phishing emails, the inclusion of a “report phishing” button within all team member emails, an integrated learning management system, and the ability to test employees on their awareness or through mock attack attempts.
Lucy is a great alternative to PhishSim (above) that goes above and beyond simply securing emails. With a free community version, this tool can be run from a web application or a Debian install. This platform helps to automate the sending of mock phishing emails, the inclusion of a “report phishing” button within all team member emails, an integrated learning management system, and the ability to test employees on their awareness or through mock attack attempts.
Spamihilator
 Spamihilator helps to prepare administrators and team members for malware-centered or phishing emails by providing an adaptive spam score for each email in your inbox. This tool utilizes a learning algorithm so spam score results improve over time. Users can train the tool to make it more adaptive to the particular needs of your organization. This tool runs on all major mail clients and saves all spam and non-spam messages in the event that a message was misdiagnosed.
Spamihilator helps to prepare administrators and team members for malware-centered or phishing emails by providing an adaptive spam score for each email in your inbox. This tool utilizes a learning algorithm so spam score results improve over time. Users can train the tool to make it more adaptive to the particular needs of your organization. This tool runs on all major mail clients and saves all spam and non-spam messages in the event that a message was misdiagnosed.
Send 2.0
 Send 2.0 utilizes military-grade encryption hosted on AWS web servers to provide the utmost assurance that messages will not be accessible until they reach the intended receiving server. Major email applications including outlook offer a “one-click install” with no configuration needed on the sending or receiving servers. A Send API allows teams with more custom email configurations to utilize Send 2.0’s high-grade encryption technology.
Send 2.0 utilizes military-grade encryption hosted on AWS web servers to provide the utmost assurance that messages will not be accessible until they reach the intended receiving server. Major email applications including outlook offer a “one-click install” with no configuration needed on the sending or receiving servers. A Send API allows teams with more custom email configurations to utilize Send 2.0’s high-grade encryption technology.
Mailwasher
 Mailwasher isn’t as customizable as other spam and phishing solutions, but it does one job incredibly well and in a user friendly way. Mailwasher combs through all incoming emails to detect malware before the emails are downloaded to your computer. For organizational clients that utilize email applications, this shores up a major way in which malware is transmitted.
Mailwasher isn’t as customizable as other spam and phishing solutions, but it does one job incredibly well and in a user friendly way. Mailwasher combs through all incoming emails to detect malware before the emails are downloaded to your computer. For organizational clients that utilize email applications, this shores up a major way in which malware is transmitted.
Tools for Internet Security
NoScript
 NoScript helps to stop cross-site scripting attacks before they begin. This tool provides an initial white-list that stops un-white-listed scripts from executing XSS or clickjacking attacks before dangerous resources load. If you find yourself on a site you trust that is being blocked by noScript, simply click a button to allow Javascript, Java, and plugin functionality to load.
NoScript helps to stop cross-site scripting attacks before they begin. This tool provides an initial white-list that stops un-white-listed scripts from executing XSS or clickjacking attacks before dangerous resources load. If you find yourself on a site you trust that is being blocked by noScript, simply click a button to allow Javascript, Java, and plugin functionality to load.
GetLinkInfo
 While not primarily a cyber security tool, GetLinkInfo (and other tools similar to it) are essential to being able to tell where tiny urls are actually sending a user. Even if you end up using a competing tool, just be aware that if you’re ever in a situation in which a tiny URL appears to be suspicious, you should put it through a tool that loads the link away from your home network.
While not primarily a cyber security tool, GetLinkInfo (and other tools similar to it) are essential to being able to tell where tiny urls are actually sending a user. Even if you end up using a competing tool, just be aware that if you’re ever in a situation in which a tiny URL appears to be suspicious, you should put it through a tool that loads the link away from your home network.
Ghostery
 Ghostery is a unique open source tool available on Windows, Mac, iOS, and Android devices. This anti-tracking tool alerts you as to what beacons, pixels, web bugs, and tracking scripts sites that you visit are using. Ghostery allows you to see what information different online service providers have on you and gives you some idea of how it is being used. Ghostery is also proactive in that it anonymenizes a great deal of your data that sites commonly seek access to.
Ghostery is a unique open source tool available on Windows, Mac, iOS, and Android devices. This anti-tracking tool alerts you as to what beacons, pixels, web bugs, and tracking scripts sites that you visit are using. Ghostery allows you to see what information different online service providers have on you and gives you some idea of how it is being used. Ghostery is also proactive in that it anonymenizes a great deal of your data that sites commonly seek access to.
Chrome Cleanup Tool
 This feature built into the Chrome browser helps to repair your install, remove malware and tracking scripts, and provide you with messaging about risky files and locations online. If you utilize the Chrome browser and have found yourself stuck with an unwanted open tab, without control of your mouse, or with malware on your computer with no idea of how it reached you, you may want to check out this beginner-friendly tool.
This feature built into the Chrome browser helps to repair your install, remove malware and tracking scripts, and provide you with messaging about risky files and locations online. If you utilize the Chrome browser and have found yourself stuck with an unwanted open tab, without control of your mouse, or with malware on your computer with no idea of how it reached you, you may want to check out this beginner-friendly tool.
Tools for Auditing of Networks and Networking
NMAP
 NMAP, as it’s name may give away, is one of the most commonly used network mapping tools in existence. With over 20 years of wide scale use, there’s a huge community to answer questions, facilitate solutions, and provide support. While there are more applications of this software than we can cover here, some of the most commonly used features include packet inspection to determine the OS, what software is installed, and behaviors of devices on your network.
NMAP, as it’s name may give away, is one of the most commonly used network mapping tools in existence. With over 20 years of wide scale use, there’s a huge community to answer questions, facilitate solutions, and provide support. While there are more applications of this software than we can cover here, some of the most commonly used features include packet inspection to determine the OS, what software is installed, and behaviors of devices on your network.
openNAC
 openNAC is a quality alternative to PacketFence (listed in the first section above). This open source network access control package includes a wide range of functionality, support for all major vendors, and a large community to help with support. A built in CMBD allows for you to create thorough documentation of your set up. And features including bulk access editing, and a wide range of customization regarding how access control rules are set up makes this a great option for your network access control.
openNAC is a quality alternative to PacketFence (listed in the first section above). This open source network access control package includes a wide range of functionality, support for all major vendors, and a large community to help with support. A built in CMBD allows for you to create thorough documentation of your set up. And features including bulk access editing, and a wide range of customization regarding how access control rules are set up makes this a great option for your network access control.
SolarWinds Network Discovery Tool
 SolarWind’s Network Discover Tool is more like a suite of tools related to network discovery and mapping. Features include SNMP collection of detailed information regarding devices on your network. Once information has been received, results are placed on a visual and explorable network topology (that updates in real time). Finally, SolarWind’s Network Discovery Tool has a number of pre-defined metrics regarding performance, uptime, and downtime of devices mapped to the network.
SolarWind’s Network Discover Tool is more like a suite of tools related to network discovery and mapping. Features include SNMP collection of detailed information regarding devices on your network. Once information has been received, results are placed on a visual and explorable network topology (that updates in real time). Finally, SolarWind’s Network Discovery Tool has a number of pre-defined metrics regarding performance, uptime, and downtime of devices mapped to the network.
Tools for SIEM
Netwrix Event Log Manager
 Netwrix Event Log Manager is a fantastic security information and event management (SIEM) tool for Windows servers. This freeware helps to bring many seperate device log files into the same view, allows users to set up unique log-based events at which they would like to receive notification, and retains an archive of past compiled log files for further analysis. If you’re a Microsoft server administrator, this free tool streamlines most command line interfaces for amalgamating an entire network’s log results.
Netwrix Event Log Manager is a fantastic security information and event management (SIEM) tool for Windows servers. This freeware helps to bring many seperate device log files into the same view, allows users to set up unique log-based events at which they would like to receive notification, and retains an archive of past compiled log files for further analysis. If you’re a Microsoft server administrator, this free tool streamlines most command line interfaces for amalgamating an entire network’s log results.
SIEMonster
 SIEMonster is a paid tool that provides access to an intuitive interface for the collection of an unlimited number of device endpoint log files. A wider range of inputs and information than most event management platforms makes SIEMonster one of the best software in its class. Information grabbed via processed log data includes human based behavior fed through the services machine learning service. An additional perk is that SIEMonster can run in the cloud or onsite.
SIEMonster is a paid tool that provides access to an intuitive interface for the collection of an unlimited number of device endpoint log files. A wider range of inputs and information than most event management platforms makes SIEMonster one of the best software in its class. Information grabbed via processed log data includes human based behavior fed through the services machine learning service. An additional perk is that SIEMonster can run in the cloud or onsite.
Splunk
 Splunk’s Security Operations Suite is one of the most well-known names within SIEM. While Splunk is big enough across security a non-security applications to have their own annual conference, their security suite has particularly made a name for itself. Quickly integrate a number of network-wide markers into a uniquely visual interface. Track devices of interest, employ machine learning, and simplify reporting and compliance with this one tool.
Splunk’s Security Operations Suite is one of the most well-known names within SIEM. While Splunk is big enough across security a non-security applications to have their own annual conference, their security suite has particularly made a name for itself. Quickly integrate a number of network-wide markers into a uniquely visual interface. Track devices of interest, employ machine learning, and simplify reporting and compliance with this one tool.
Alienvault OSSIM
 Alienvault’s Open Source SIEM, offered by AT&T Cyber Security, is perhaps the most widely employed SIEM solution. While a suite of security tools is offered around SIEM, some of the most noteworthy include asset discovery and inventory, event correlation, behavioral monitoring, intrusion detection, a very visual dashboard to track all of these concerns, and an active community for support measures.
Alienvault’s Open Source SIEM, offered by AT&T Cyber Security, is perhaps the most widely employed SIEM solution. While a suite of security tools is offered around SIEM, some of the most noteworthy include asset discovery and inventory, event correlation, behavioral monitoring, intrusion detection, a very visual dashboard to track all of these concerns, and an active community for support measures.
Tools for Scanning Vulnerabilities
OpenVAS
 OpenVAS or Open Vulnerability Assessment System, is supported by Greenbone Networks since 2009. The project is one of the most robust frameworks for vulnerability testing and features unauthenticated, authenticated, and high and low-level industrial protocols. Daily updates as well as a list of over 50,000 pre-made vulnerability tests shared with the community make this VAS the top choice for many cyber security professionals.
OpenVAS or Open Vulnerability Assessment System, is supported by Greenbone Networks since 2009. The project is one of the most robust frameworks for vulnerability testing and features unauthenticated, authenticated, and high and low-level industrial protocols. Daily updates as well as a list of over 50,000 pre-made vulnerability tests shared with the community make this VAS the top choice for many cyber security professionals.
Nessus
 Nessus is more than a suite of tools, but rather an expert-level community that has helped to discover and deploy information on over 100 zero-day exploits within the last three years to application developers. Over 100 new plugins weekly respond to the latest in malware and exploits targeting applications. With information on the latest exploits updated in live time, a host of reporting and compliance tools, and a number of scanning tools, Nessus is the #1 trusted application vulnerability scanner in the game.
Nessus is more than a suite of tools, but rather an expert-level community that has helped to discover and deploy information on over 100 zero-day exploits within the last three years to application developers. Over 100 new plugins weekly respond to the latest in malware and exploits targeting applications. With information on the latest exploits updated in live time, a host of reporting and compliance tools, and a number of scanning tools, Nessus is the #1 trusted application vulnerability scanner in the game.
Burp Suite
 Portswigger’s Burp Suite of tools is available in three tiers ranging from a free hobbyist or researcher suite, through an enterprise-level solution. The Burp Suite of tools offers a cutting-edge web vulnerability scanner that checks for over 100 types of common web exploits updated routinely. Unlimited scalability and schedule or repeat scans help to keep your web presence or application continually surveilled. While paid versions may be beyond the scope of even small businesses, a host of manual tools are available for free to anyone.
Portswigger’s Burp Suite of tools is available in three tiers ranging from a free hobbyist or researcher suite, through an enterprise-level solution. The Burp Suite of tools offers a cutting-edge web vulnerability scanner that checks for over 100 types of common web exploits updated routinely. Unlimited scalability and schedule or repeat scans help to keep your web presence or application continually surveilled. While paid versions may be beyond the scope of even small businesses, a host of manual tools are available for free to anyone.
Shodan
 Lest we forget that vulnerabilities now exist in a wide range of devices (think refrigerators, cars, voice assistants), Shodan bills itself out as the “search engine for the internet of things.” Utilized by over half of Fortune 100 companies, Shodan provides real time intelligence on all discoverable internet-connected devices. Use real-time scanning to see what could be compromising your internet-of-things devices. Or use competitive intelligence regarding internet-connected hardware that’s at risk.
Lest we forget that vulnerabilities now exist in a wide range of devices (think refrigerators, cars, voice assistants), Shodan bills itself out as the “search engine for the internet of things.” Utilized by over half of Fortune 100 companies, Shodan provides real time intelligence on all discoverable internet-connected devices. Use real-time scanning to see what could be compromising your internet-of-things devices. Or use competitive intelligence regarding internet-connected hardware that’s at risk.
Tools for Penetration Testing
Aircrack-ng
 Aircrack-ng is a command line-based wifi auditing and attacking suite of tools. Primarily built for Linux, Aircrack-ng also works on most major operating systems. Build entirely on command line tools, Aircrack-ng allows for robust scripting. Many applications have taken advantage of this to build their services on Aircrack-ng. Exploit frameworks available through Aircrack-ng include packet rupturing, capturing, exportation; deauthentication and fake access point attacks; the checking of wifi card and drive capabilities; and cracking of lesser encryption methods.
Aircrack-ng is a command line-based wifi auditing and attacking suite of tools. Primarily built for Linux, Aircrack-ng also works on most major operating systems. Build entirely on command line tools, Aircrack-ng allows for robust scripting. Many applications have taken advantage of this to build their services on Aircrack-ng. Exploit frameworks available through Aircrack-ng include packet rupturing, capturing, exportation; deauthentication and fake access point attacks; the checking of wifi card and drive capabilities; and cracking of lesser encryption methods.
John the Ripper
 John the Ripper is one of the most widely used password-cracking tools. Historically for weak Unix-based passwords, John the Ripper is available for many operating systems today. For Windows and Android, consider the Hash Suite, a related piece of software built by the makers of John the Ripper. Additional offerings of this tool include a collection of common word lists for passwords within 20+ languages.
John the Ripper is one of the most widely used password-cracking tools. Historically for weak Unix-based passwords, John the Ripper is available for many operating systems today. For Windows and Android, consider the Hash Suite, a related piece of software built by the makers of John the Ripper. Additional offerings of this tool include a collection of common word lists for passwords within 20+ languages.
Metasploit
 MetaSploit is the world’s most utilized penetration testing framework. This open source collaboration between Source 7 and the broader community is available in a free and enterprise edition (and both are quite powerful). The range of exploit types possible of enacting through this framework is really quite staggering, and beyond the scope of this piece. But just know that as the most widely utilized penetration testing framework (and an open source one), there’s a huge community routinely posting guides, improving the framework, and offering support.
MetaSploit is the world’s most utilized penetration testing framework. This open source collaboration between Source 7 and the broader community is available in a free and enterprise edition (and both are quite powerful). The range of exploit types possible of enacting through this framework is really quite staggering, and beyond the scope of this piece. But just know that as the most widely utilized penetration testing framework (and an open source one), there’s a huge community routinely posting guides, improving the framework, and offering support.
Kali Linux
 Kali Linux is an entire operating system build around advanced penetration testing. This Debian-based OS comes with several hundred penetration testing and ethical hacking tools (600+) pre-installed and can be molded to your heart’s content. With a small trusted group of contributors as the only members of the dev crew allowed to actually interact with repositories, all new pushes are verified to be secure.
Kali Linux is an entire operating system build around advanced penetration testing. This Debian-based OS comes with several hundred penetration testing and ethical hacking tools (600+) pre-installed and can be molded to your heart’s content. With a small trusted group of contributors as the only members of the dev crew allowed to actually interact with repositories, all new pushes are verified to be secure.
Tools for Breach Alarms
SpyCloud
 SpyCloud is one of a handful of top services that crawl all corners of the web to determine ways in which you or your team members data has been breached. Usable at scale, SpyCloud helps some of the largest online service providers inform users of passwords that have already been breached for others. Additional features include a fraud investigation database, an API for integrating SpyCloud into your SIEM, and password enforcement across devices and services.
SpyCloud is one of a handful of top services that crawl all corners of the web to determine ways in which you or your team members data has been breached. Usable at scale, SpyCloud helps some of the largest online service providers inform users of passwords that have already been breached for others. Additional features include a fraud investigation database, an API for integrating SpyCloud into your SIEM, and password enforcement across devices and services.
HaveIBeenPwned
 HaveIBeenPwned has perhaps the largest and most regularly updated directory of email data breaches. A quick free search determines whether one email address was part of a large data breach as well as whether the email and accompanying details were pasted to a public-facing page. Their paid service offers automatic updates when breaches are discovered.
HaveIBeenPwned has perhaps the largest and most regularly updated directory of email data breaches. A quick free search determines whether one email address was part of a large data breach as well as whether the email and accompanying details were pasted to a public-facing page. Their paid service offers automatic updates when breaches are discovered.
BreachAlarm
 BreachAlarm is (surprise, surprise) a breach alarm service that focuses on intelligence regarding passwords that have been exposed. They have one of (if not the largest) database of stolen passwords as well as information on whether your passwords have been pasted to public-facing pages online. Used in conjunction with other services you can track down the root causes of some breaches through third-party vendors.
BreachAlarm is (surprise, surprise) a breach alarm service that focuses on intelligence regarding passwords that have been exposed. They have one of (if not the largest) database of stolen passwords as well as information on whether your passwords have been pasted to public-facing pages online. Used in conjunction with other services you can track down the root causes of some breaches through third-party vendors.
Tools for Management And Attacking of Passwords
HashCat
 HashCat is the “gold standard” for password recovery system that implements over 200 hash types to discover passwords on locked machines. HashCat works on most major operating systems, and utilizes both CPUs and GPUs to crack encrypted passwords more quickly than most competitors. Perhaps best of all, HashCat is both free and open source.
HashCat is the “gold standard” for password recovery system that implements over 200 hash types to discover passwords on locked machines. HashCat works on most major operating systems, and utilizes both CPUs and GPUs to crack encrypted passwords more quickly than most competitors. Perhaps best of all, HashCat is both free and open source.
CyberArk’s Enterprise Password Vault
 While a bit more than most uses need, CyberArks’s Enterprise Password Vault can scale indefinitely and provides a secure and centralized environment for both passwords and hash keys. This information may be stored on-premises, in a hybrid solution, or in the cloud. For on-premises jobs, however, the price tag is much higher and includes a c.$25,000 EVP server installation.
While a bit more than most uses need, CyberArks’s Enterprise Password Vault can scale indefinitely and provides a secure and centralized environment for both passwords and hash keys. This information may be stored on-premises, in a hybrid solution, or in the cloud. For on-premises jobs, however, the price tag is much higher and includes a c.$25,000 EVP server installation.
LastPass Enterprise and Team
 LastPass offers both enterprise and team accounts that are much, much more affordable than the CyberArk solution above. For small business, an intuitive dashboard gives intelligence regarding when passwords were last changed, overall security score, automation of changing passwords, and advice on how to most effectively shore up your organization’s current password set up.
LastPass offers both enterprise and team accounts that are much, much more affordable than the CyberArk solution above. For small business, an intuitive dashboard gives intelligence regarding when passwords were last changed, overall security score, automation of changing passwords, and advice on how to most effectively shore up your organization’s current password set up.
Cain and Able
 Cain and Able is a longstanding tool built for the Windows operating system. A variety of techniques for discovering or cracking passwords are available through this tool including brute force attacks, network sniffing, and dictionary attacks.
Cain and Able is a longstanding tool built for the Windows operating system. A variety of techniques for discovering or cracking passwords are available through this tool including brute force attacks, network sniffing, and dictionary attacks.
Tools for Encryption
SoftEther
 SoftEther is an open source VPN solution available for free personal or commercial use on most common operating systems. A built in “clone” service can help you migrate from an existing Windows VPN or OpenVPN set up. Additional features include low latency, high throughput, and low firewall resistance. As it’s open source, you can even build your own project on top of SoftEther.
SoftEther is an open source VPN solution available for free personal or commercial use on most common operating systems. A built in “clone” service can help you migrate from an existing Windows VPN or OpenVPN set up. Additional features include low latency, high throughput, and low firewall resistance. As it’s open source, you can even build your own project on top of SoftEther.
Signal
 Signal is literally “just” a messaging app. But it’s known to be one of the most secure ways to communicate between individuals and small teams. And by messaging, we do mean a variety of message types, including live voice and video. Applications are available for desktop, iOS, and Android, and employ some of the latest (and most practical) encryption solutions for client to client messaging.
Signal is literally “just” a messaging app. But it’s known to be one of the most secure ways to communicate between individuals and small teams. And by messaging, we do mean a variety of message types, including live voice and video. Applications are available for desktop, iOS, and Android, and employ some of the latest (and most practical) encryption solutions for client to client messaging.
NoMoreRansom
 When a Ransomware attack takes over your device, your data is encrypted and held ransom. Even if you pay the ransom, there’s no guarantee that you’ll get your data back. NoMoreRansom offers a suite of known decryption keys for well-known ransomware attacks. Each decryption key has a handy implementation guide that most cyber security professionals should be able to follow.
When a Ransomware attack takes over your device, your data is encrypted and held ransom. Even if you pay the ransom, there’s no guarantee that you’ll get your data back. NoMoreRansom offers a suite of known decryption keys for well-known ransomware attacks. Each decryption key has a handy implementation guide that most cyber security professionals should be able to follow.
BitLocker
 BitLocker is the built-in encryption feature included on Windows machines with Vista or newer operating systems. AES encryption is used for the entirety of the disk space. Each segment of the disk is placed into its own cipher block chain. Bitlocker can be managed from Powershell and in addition to encrypting the contents of individual computers on your network, can also encrypt the contents of Windows-running servers.
BitLocker is the built-in encryption feature included on Windows machines with Vista or newer operating systems. AES encryption is used for the entirety of the disk space. Each segment of the disk is placed into its own cipher block chain. Bitlocker can be managed from Powershell and in addition to encrypting the contents of individual computers on your network, can also encrypt the contents of Windows-running servers.
Suites of Tools of Cyber Security Frameworks
Resolver Threat and Vulnerability Management Software
 Resolver offers a full suite of cyber security tools and services. Perhaps their product most pertinent to this list is their threat and vulnerability management software. This suite of software provides an intuitive dashboard through which to integrate all of your risk management data sources. Mine down deeper with tools like migration verification, classification of assets, ranking of threat levels, and automated data collection.
Resolver offers a full suite of cyber security tools and services. Perhaps their product most pertinent to this list is their threat and vulnerability management software. This suite of software provides an intuitive dashboard through which to integrate all of your risk management data sources. Mine down deeper with tools like migration verification, classification of assets, ranking of threat levels, and automated data collection.
Acunetix
 Acunetix offers an entire suite of offerings surrounding web security including a website security scanner, a vulnurability scanner, an external vulnurability scanner, and a WordPress vulnurability scanner. If you’re tasked with client-facing web properties, Acunetix provides an integrated suite of organizational tools including workflow management, tagging tasks and threats as high priority, and automated build tools.
Acunetix offers an entire suite of offerings surrounding web security including a website security scanner, a vulnurability scanner, an external vulnurability scanner, and a WordPress vulnurability scanner. If you’re tasked with client-facing web properties, Acunetix provides an integrated suite of organizational tools including workflow management, tagging tasks and threats as high priority, and automated build tools.
Solarwinds Threat Monitor
 SolarWind’s Threat Monitor is a suite of tools allowing for discovery of, tracking of, and remediation of threats. The suite comes with a built in SIEM, continuous threat intelligence, ability to correlate logs across your network, archived logs, a network and a host intrusion detection system, and enhanced log search abilities.
SolarWind’s Threat Monitor is a suite of tools allowing for discovery of, tracking of, and remediation of threats. The suite comes with a built in SIEM, continuous threat intelligence, ability to correlate logs across your network, archived logs, a network and a host intrusion detection system, and enhanced log search abilities.
Tools for Cyber Security Reconnaissance
The Harvester
 One of the many tools within Kali Linux is the Harvester. The Harvester is essentially a web scraper that looks for subdomain names, email addresses, open ports, and employee names from a given location. This can be used for preparing for a pentest, or to identify information about your organization that is presently online.
One of the many tools within Kali Linux is the Harvester. The Harvester is essentially a web scraper that looks for subdomain names, email addresses, open ports, and employee names from a given location. This can be used for preparing for a pentest, or to identify information about your organization that is presently online.
OSINT Framework
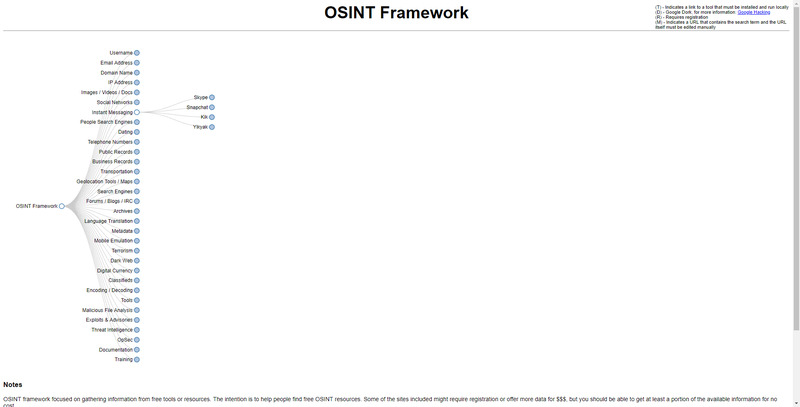 The OSINT Framework isn’t a tool you install, but rather a conceptual framework used as a tool to discern common sources of data online. The framework is periodically updated, and offers a range of categories through which data about a target individual or businesses can be gathered from publicly available sources. While some sources may require your registration, or for you to pay money for data, they typically are publicly accessible.
The OSINT Framework isn’t a tool you install, but rather a conceptual framework used as a tool to discern common sources of data online. The framework is periodically updated, and offers a range of categories through which data about a target individual or businesses can be gathered from publicly available sources. While some sources may require your registration, or for you to pay money for data, they typically are publicly accessible.
CheckUserNames
 CheckUserNames is a great reconnaissance tool that can be used to find footprints in usernames across over 100 social media services. If you’re looking for data on usage of different platforms as a sort of pre-reconnaissance, CheckUserNames can be a great tool for doing so.
CheckUserNames is a great reconnaissance tool that can be used to find footprints in usernames across over 100 social media services. If you’re looking for data on usage of different platforms as a sort of pre-reconnaissance, CheckUserNames can be a great tool for doing so.
Cynsys
 Censys is the second “search engine for connected devices” we’ve included in our list. One unique aspect of Cynsys results is that they include geographic and full range of technical data from port 80 and 443 of connected devices. Use this service to locate a compromised machine, to determine the location or technical specifications of a machine attacking your network, and more, or simply to determine weak points in your own defenses.
Censys is the second “search engine for connected devices” we’ve included in our list. One unique aspect of Cynsys results is that they include geographic and full range of technical data from port 80 and 443 of connected devices. Use this service to locate a compromised machine, to determine the location or technical specifications of a machine attacking your network, and more, or simply to determine weak points in your own defenses.
Tools for Learning Cyber Security Tools and Concepts
Kali Linux Revealed
 As Kali Linux comes with perhaps the single largest collection of cyber security tools, and particularly tools that relate to penetration testing and ethical hacking, learning how to use and modify this system takes you a long way towards using many cyber security tools. One resource that Kali.org specifically recommends is the Kali Linux Revealed book. You can order a copy on Amazon or download a free e-book version.
As Kali Linux comes with perhaps the single largest collection of cyber security tools, and particularly tools that relate to penetration testing and ethical hacking, learning how to use and modify this system takes you a long way towards using many cyber security tools. One resource that Kali.org specifically recommends is the Kali Linux Revealed book. You can order a copy on Amazon or download a free e-book version.
Springboard
 Springboard is a longtime leader in information technology and cyber security education. Their list of some of the best locations to gain free information and training in cyber security is one of the most comprehensive and best researched online. While there are certainly paid cyber security training resources out there as well, the locations in their list provide plenty of educational opportunities for everyone from beginning cyber security students through seasoned cyber security professionals.
Springboard is a longtime leader in information technology and cyber security education. Their list of some of the best locations to gain free information and training in cyber security is one of the most comprehensive and best researched online. While there are certainly paid cyber security training resources out there as well, the locations in their list provide plenty of educational opportunities for everyone from beginning cyber security students through seasoned cyber security professionals.
Cybrary
 Cybrary is a collection of over 500 free cyber security courses that range from entire certification prep courses to small one-day introductions. Many of the most popular vendors post their own courses on Cybrary, and you can sort by difficulty (easy, intermediate, and advanced). For both new cyber security students (or professionals) or seasoned professionals, Cybrary is one of the best free resources available for learning about information assurance.
Cybrary is a collection of over 500 free cyber security courses that range from entire certification prep courses to small one-day introductions. Many of the most popular vendors post their own courses on Cybrary, and you can sort by difficulty (easy, intermediate, and advanced). For both new cyber security students (or professionals) or seasoned professionals, Cybrary is one of the best free resources available for learning about information assurance.
Open Security Training
 Open Security Training offers a host of intermediate to advanced-level courses. Topics are wide ranging and cover areas uncovered by Cybrary’s large database of courses. Many courses are programming heavy, which can be hard to find in open online courses. A sampling of topics includes cryptoanalysis, reverse engineering malware, software exploits, and rootkits.
Open Security Training offers a host of intermediate to advanced-level courses. Topics are wide ranging and cover areas uncovered by Cybrary’s large database of courses. Many courses are programming heavy, which can be hard to find in open online courses. A sampling of topics includes cryptoanalysis, reverse engineering malware, software exploits, and rootkits.