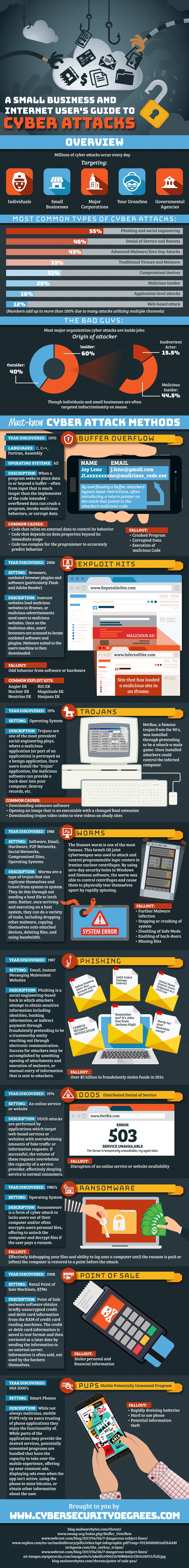
A Small Business and Internet User’s Guide to Cyber Attacks
—
Millions of cyber attacks occur every day
Targetting
Individuals
Small Businesses
Major Corporations
Your Grandma
Governmental Agencies
—
Most Common Types of Cyber Attacks:[4]
Phishing and social engineering: 55%
Denial of Service and Botnets: 46%
Advanced Malware/Zero Day Attacks: 43%
Traditional Viruses and Malware: 33%
Comprimised devices: 31%
Malicious Insider: 25%
Application-level attacks: 16%
Web-based attack: 12%
(Numbers add up to more than 100% due to many attacks utilizing multiple channels)
—
The bad guys[3]:
Most major organization cyber attacks are inside jobs:
Origin of attacker
Outsider: 40%
Insider: 60%
–Inadvertent Actor: 15.5%
–Malicious Insider: 44.5%
Though individuals and small businesses are often targeted indiscriminately en masse.
—-
Must-know cyber attack methods:
Buffer Overflow[1][2]
–Year discovered: 1970
–Languages: C, C++, Fortran, Assembly
–Operating Systems: All
–Description:
When a program seeks to place data in or beyond a buffer — often from input that is much longer than the implementer of the code intended — overflowed data can crash a program, invoke malicious behaviors, or corrupt data.
–Visual Example:
Two column chart in what looks like a phone app, in one column it has names, in another their email address, in a working example the first column is filled with a name (Jay Leno) and the second column might be filled with j.leno@gmail.com. In an example of buffer overflow, the first column would be filled with Jay Lxxxxxxxxxxxxxxxxxxxno@malicious_code.exe, where the length of the number of x’s fills up the first column, and the program pushes ‘malicious_code.exe’ into the second column. A caption for that second column in the second example could be: “By overflowing a buffer, attackers bypass input restrictions, often introducing a return pointer on the stack that points to the attackers malicious code.”
–Common Causes:
-Code that relies on external data to control its behaviour
-Code that depends on data properties beyond its immediate scope
-Code too complex for the programmer to accurately predict behavior
–Fallout:
Crashed Program
Corrupted Data
Execution of malicious Code
Exploit Kits
–Year discovered: 2006
–Setting: Browsers, outdated browser plugins and software (particularly Flash and Adobe Reader)
–Description: Insecure websites load malicious websites in iframes, or malicious advertisements send users to malicious websites. Once on the malicious sites, users’ browsers are scanned to locate outdated software and plugins. Malware suited to the users machine is then downloaded.
–Visual Example:
Example of otherwise reputable site with a malicious ad highlighted–then the word or–then an infected site that has loaded a malicious site in an iframe (label iframe).
–Fallout:
Odd behavior from software or hardware
–Common Exploit Kits
Angler EK
Nuclear EK
Neutrino EK
RIG EK
Magnitude EK
Hanjuan EK
Trojans
–Year discovered: 1974
–Setting: Operating System
–Description: Trojans are one of the most prevalent social engineering ploys, where a malicious application (or part of an application) is portrayed as a benign application. Once users install the “trojan” application, the malicious software can provide a backdoor into your computer, destroy records, etc.
–Visual Example:
Show example screen from NetBus[5], a famous trojan from the 90’s disguised as a whack-a-mole game. Once it was installed the attacker had actions to the functions in the image at citation [5].Text: “NetBus a famous trojan from the 90’s was installed through pretending to be a whack-a-mole game. Once installed attackers could control the infected computer.”
–Common Causes:
Downloading unknown software
Opening an image that is an executable with a changed final extension
Downloading trojen video codecs to view videos on shady sites
Worms
–Year discovered: 1988
–Setting: Software, Email, Hardware, P2P Networks, Social Networks, Compromised Sites, Operating Systems
–Description: Worms are a type of trojan that can replicate themselves and travel from system to system. They do this through not needing a host file to latch onto. Rather, once arriving and executing on a host system, they can do a variety of tasks, including dropping other malware, copying themselves onto attached devices, deleting files, and using bandwidth.
–Visual Example:
The Stuxnet worm is one of the most famous. This Israeli-US joint cyberweapon was used to attack and control programmable logic centers in Iranian nuclear centrifuges. By using zero-day security holes in Windows and Siemens software, the worm was able to control centrifuges and cause them to physically tear themselves apart by rapidly spinning.
–Fallout:
Further Malware infection
Stopping or crashing of system
Disabling of Safe Mode
Enabling of backdoors
Missing files
Phishing
–Year discovered: 1987
–Setting: Email, Instant Messaging Malevolent Websites
–Description: Phishing is a social engineering-based hack in which attackers attempt to obtain sensitive information including identities, banking information, or indirect payment through fraudulently pretending to be a trustworthy entity reaching out through electronic communication. Success for attackers may be accomplished by unwitting opening of attachments and execution of malware, or manual entry of information that is sent to attackers.
–Visual Example:
Show a number of screens with emails received, highlight the following typical phishing scheme example titles:[6]
Remember me? It’s John Doe from Jackson High!
Online Banking Alert: Your Account will be Deactivated.
USPS: Failed Package Delivery
United States District Court: Subpoena in a civil case
CAMPUS SECURITY NOTIFICATION
Ready for your Hawaiian vacay?
Update your direct deposit to receive your tax refund
Show “urgent” markers toggled for emails.
–Fallout:
Over $5 billion in fraudulently stolen funds in 2014
Distributed Denial of Service (DDOS)
–Year Discovered: 1974
–Setting: An online service or website
–Description: DDOS attacks are performed by applications which target web-based services or websites with overwhelming amounts of fake traffic or information requests. If successful, the volume of these requests The volume of these requests
–Visual Example:
citation [7] shows an example, maybe replace the URL with some well known service like netflix
–Fallout:
Disruption of an online service or website availability
Ransomware
–Year Discovered: 1980’s
–Setting: Operating System
–Description: Ransomware is a form of cyber attack to locks users out of their computer and/or often encrypts users personal files, offering to unlock the computer and decrypt files if the user pays a ransom.
–Visual Example:
examples of screenshots of ransomware screens may be found here: https://www.google.com/search?q=examples+of+ransomware+screens&source=lnms&tbm=isch&sa=X&ved=0ahUKEwjRm9jfoJbVAhWIeT4KHSrJB5AQ_AUICigB&biw=1848&bih=1014
Particularly prevalent are often badges pretending to be law enforcement as well as timers.
–Fallout:
Effectively kidnapping your files and ability to log onto a computer until the ransom is paid or (often) the computer is restored to a point before the attack.
Point of Sale
–Year Discovered: 2008
–Setting: Retail Point of Sale Machines, ATMs
–Description: Point of Sale malware software obtains briefly unencrypted credit and debit card information from the RAM of credit card reading machines. The credit or debit card information is saved in text format and then retrieved at a later date by sending the information to an external server. Information is often sold, not used by the hackers themselves.
–Visual Example: screenshots of the readout obtained from a POS malware software may be found at the bottom of the page of citation [8]
–Fallout: stolen personal and financial information
Mobile Potentially Unwanted Program (PUPS)
–Year Discovered–Mid 2000’s
–Setting: Smart Phones
–Description: While not always malicious, mobile PUPS rely on users trusting of phone applications they enjoy the functionality of. While parts of the application may provide the desired services, potentially unwanted programs are bundled that have the capacity to take over the mobile experience, offering up near constant ads, displaying ads even when the app isn’t active, using the phone to mine bitcoins, or obtain other information about the user.
–Visual Example: A phone screen overtaken by full screen ads
–Fallout: Rapidly draining batteries, hard to use phone, potential information theft
Brought to you by www.CyberSecurityDegrees.com
[1]https://blog.malwarebytes.com/threat/
[2]https://www.owasp.org/index.php/Buffer_Overflow
[3]https://www.webroot.com/blog/2017/04/06/7-dangerous-subject-lines/
[4]https://www.sophos.com/en-us/medialibrary/pdfs/other/apt-infographic.pdf?cmp=70130000001xIObAAM
[5]https://techgenix.com/the_netbus_trojan/
[6]https://www.webroot.com/blog/2017/04/06/7-dangerous-subject-lines/
[7]https://a4-images.myspacecdn.com/images04/4/a8edfce90651476986b63c53b5c06913/full.jpg
[8]https://blog.malwarebytes.com/threats/point-of-sale-pos/
